Question 131
A technician has installed a new AAA server, which will be used by the network team to control access to a company's routers and switches. The technician completes the configuration by adding the network team members to the NETWORK_TEAM group, and then adding the NETWORK_TEAM group to the appropriate ALLOW_ACCESS access list. Only members of the network team should have access to the company's routers and switches.

Members of the network team successfully test their ability to log on to various network devices configured to use the AAA server. Weeks later, an auditor asks to review the following access log sample:
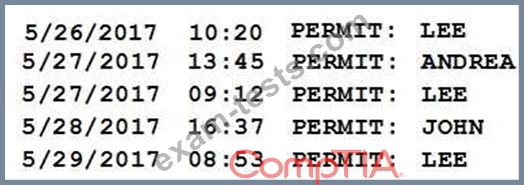
Which of the following should the auditor recommend based on the above information?

Members of the network team successfully test their ability to log on to various network devices configured to use the AAA server. Weeks later, an auditor asks to review the following access log sample:

Which of the following should the auditor recommend based on the above information?
Question 132
An office recently completed digitizing all its paper records. Joe, the data custodian, has been tasked with the disposal of the paper files, which include:
* Intellectual property
* Payroll records
* Financial information
* Drug screening results
Which of the following is the BEST way to dispose of these items?
* Intellectual property
* Payroll records
* Financial information
* Drug screening results
Which of the following is the BEST way to dispose of these items?
Question 133
A user recently entered a username and password into a recruiting application website that had been forged to look like the legitimate site. Upon Investigation, a security analyst identifies the following:
* The legitimate website's IP address is 10.1.1.20 and eRecruit.local resolves to this IP.
* The forged website's IP address appears to be 10.2.12.99. based on NetFlow records.
* All three of the organization's DNS servers show the website correctly resolves to the legitimate IP.
* DNS query logs show one of the three DNS servers returned a result of 10.2.12.99 (cached) at the approximate time of the suspected compromise.
Which of the following MOST likely occurred?
* The legitimate website's IP address is 10.1.1.20 and eRecruit.local resolves to this IP.
* The forged website's IP address appears to be 10.2.12.99. based on NetFlow records.
* All three of the organization's DNS servers show the website correctly resolves to the legitimate IP.
* DNS query logs show one of the three DNS servers returned a result of 10.2.12.99 (cached) at the approximate time of the suspected compromise.
Which of the following MOST likely occurred?
Question 134
A company wants to host a publicly available server that performs the following functions:
Evaluates MX record lookup
Can perform authenticated requests for A and AAA records
Uses RRSIG
Which of the following should the company use to fulfill the above requirements?
Evaluates MX record lookup
Can perform authenticated requests for A and AAA records
Uses RRSIG
Which of the following should the company use to fulfill the above requirements?
Question 135
A Chief Executive Officer (CEO) suspects someone in the lab testing environment is stealing confidential
information after working hours when no one else is around. Which of the following actions can help to
prevent this specific threat?
information after working hours when no one else is around. Which of the following actions can help to
prevent this specific threat?

