Question 136
After a user reports slow computer performance, a system administrator detects a suspicious file, which was installed as part of a freeware software package. The systems administrator reviews the output below:
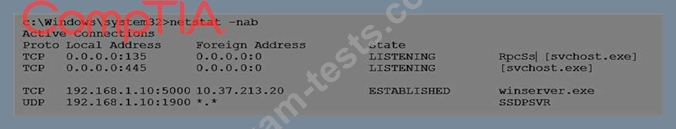
Based on the above information, which of the following types of malware was installed on the user's computer?

Based on the above information, which of the following types of malware was installed on the user's computer?
Question 137
Company A has acquired Company B.
Company A has different domains spread globally, and typically migrates its acquisitions infrastructure under its own domain infrastructure. Company B, however, cannot be merged into Company A's domain infrastructure. Which of the following methods would allow the two companies to access one another's resources?
Company A has different domains spread globally, and typically migrates its acquisitions infrastructure under its own domain infrastructure. Company B, however, cannot be merged into Company A's domain infrastructure. Which of the following methods would allow the two companies to access one another's resources?
Question 138
A company is terminating an employee for misbehavior.
Which of the following steps is MOST important in the process of disengagement from this employee?
Which of the following steps is MOST important in the process of disengagement from this employee?
Question 139
A security administrator is given the security and availability profiles for servers that are being deployed.
* Match each RAID type with the correct configuration and MINIMUM number of drives.
* Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
* All drive definitions can be dragged as many times as necessary
* Not all placeholders may be filled in the RAID configuration boxes
* If parity is required, please select the appropriate number of parity checkboxes
* Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
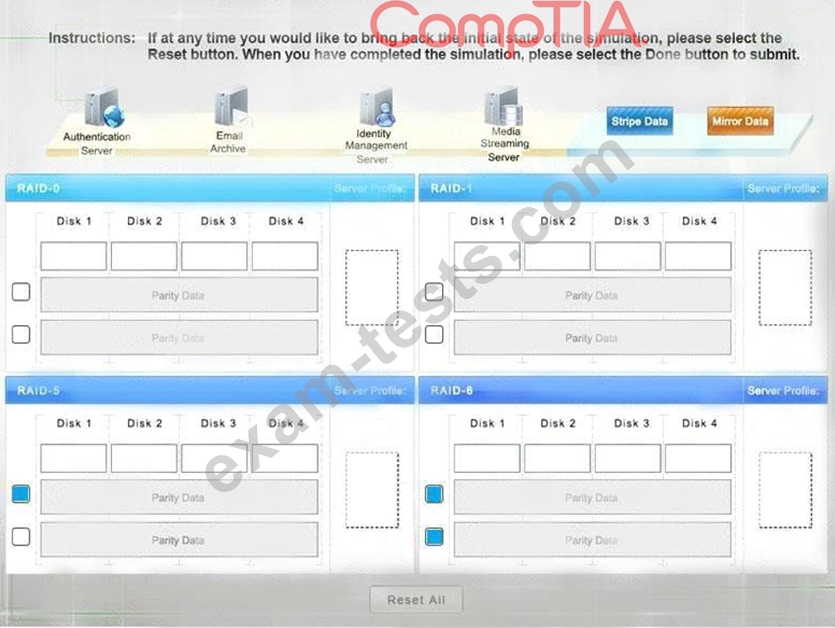
* Match each RAID type with the correct configuration and MINIMUM number of drives.
* Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
* All drive definitions can be dragged as many times as necessary
* Not all placeholders may be filled in the RAID configuration boxes
* If parity is required, please select the appropriate number of parity checkboxes
* Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

Question 140
Which of the following attacks can be used to exploit a vulnerability that was created by untrained users?



