Question 31
Which event artifact is used to identity HTTP GET requests for a specific file?
Question 32
Which two pieces of information are collected from the IPv4 protocol header? (Choose two.)
Question 33
Refer to the exhibit.
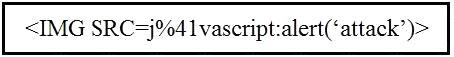
Which kind of attack method is depicted in this string?
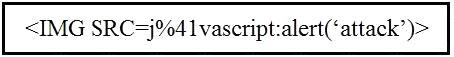
Which kind of attack method is depicted in this string?
Question 34
An analyst received an alert on their desktop computer showing that an attack was successful on the host.
After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
Question 35
Refer to the exhibit.
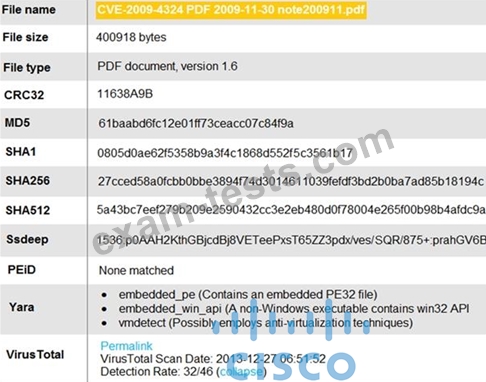
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email.
What is the state of this file?

An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email.
What is the state of this file?

