Question 36
Which type of data consists of connection level, application-specific records generated from network traffic?
Question 37
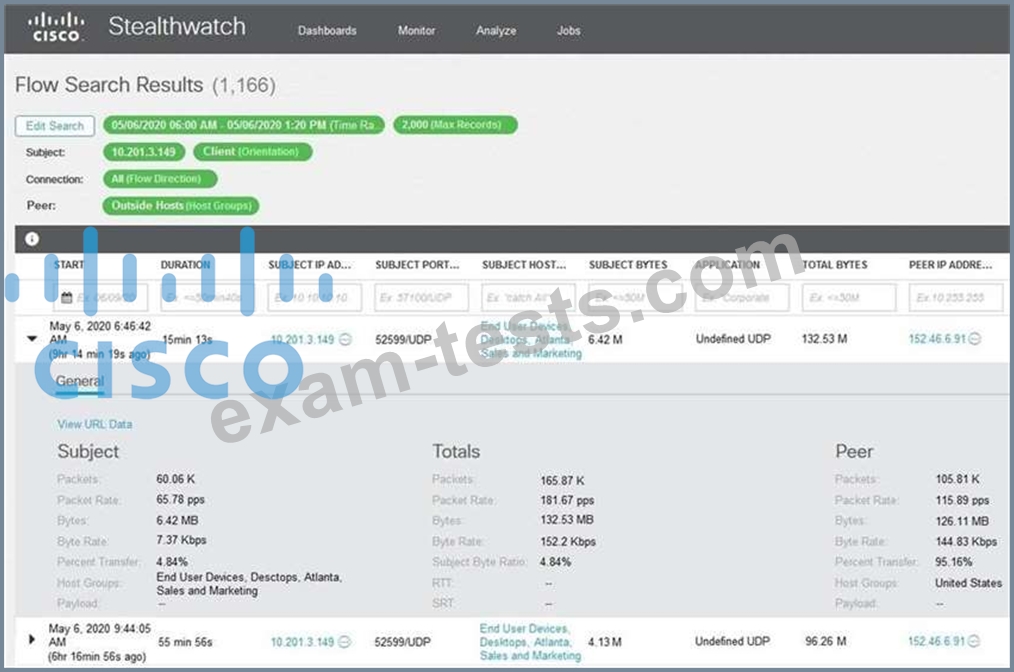
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
Question 38
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
Question 39
Refer to the exhibit.
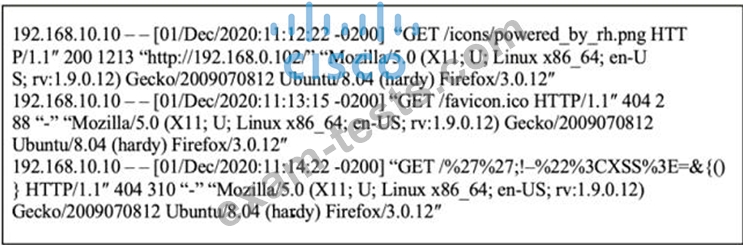
What is occurring within the exhibit?

What is occurring within the exhibit?
Question 40
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?

