Question 26
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
Which testing method did the intruder use?
Question 27
Refer to the exhibit.

In which Linux log file is this output found?

In which Linux log file is this output found?
Question 28
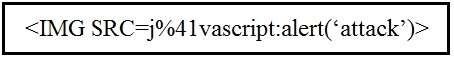
Refer to the exhibit. Which kind of attack method is depicted in this string?
Question 29
How does certificate authority impact a security system?
Question 30
Refer to the exhibit.
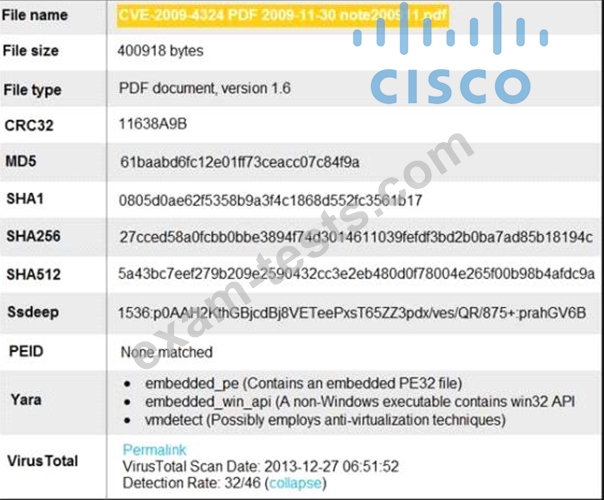
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?

An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?

