Question 6
Which incidence response step includes identifying all hosts affected by an attack?
Question 7
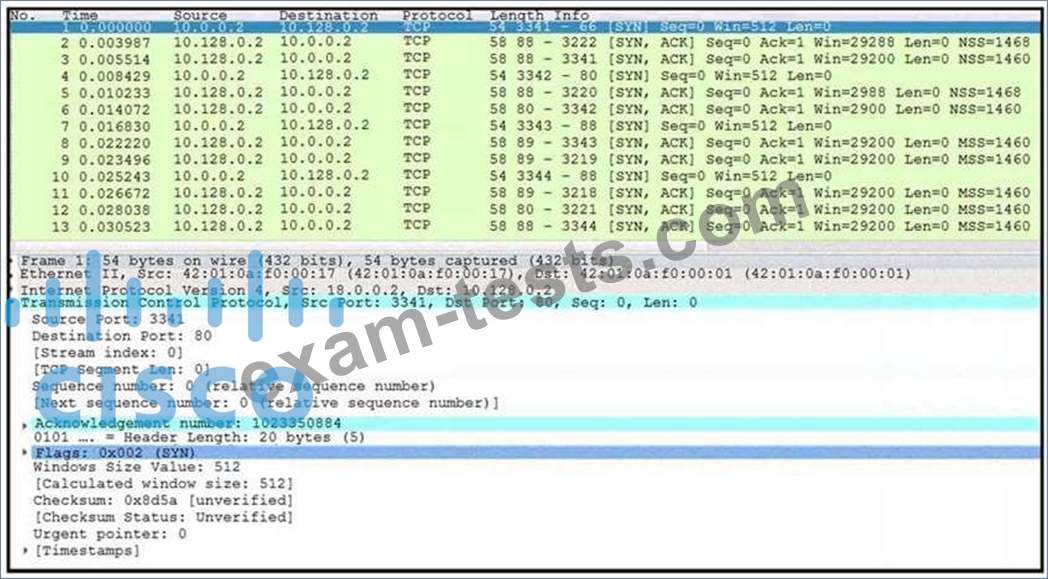
Refer to the exhibit. What is occurring in this network traffic?
Question 8
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
Question 9
Which system monitors local system operation and local network access for violations of a security policy?
Question 10
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email.
When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?

