Question 11
A user received a malicious attachment but did not run it.
Which category classifies the intrusion?
Which category classifies the intrusion?
Question 12
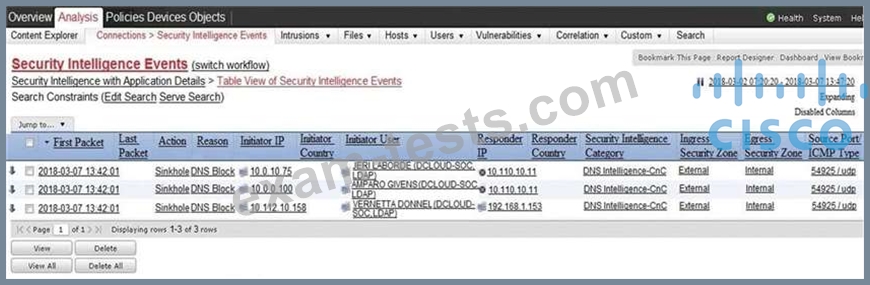
Refer to the exhibit. Which two elements in the table are parts of the 5-tuple? (Choose two.)
Question 13
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
Question 14
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
Question 15
W[^t is vulnerability management?

