Question 136
What is the difference between discretionary access control (DAC) and role-based access control (RBAC)?
Question 137
W[^t is vulnerability management?
Question 138
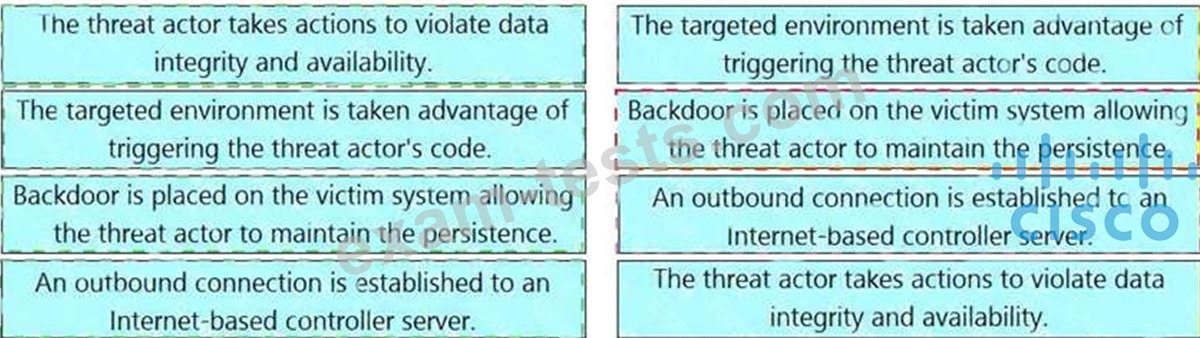
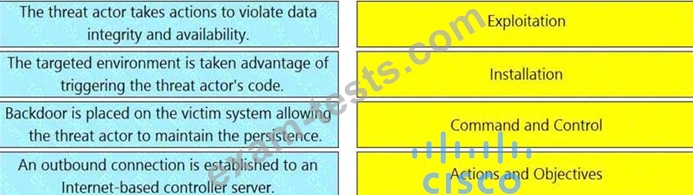
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.

Question 139
Refer to the exhibit.
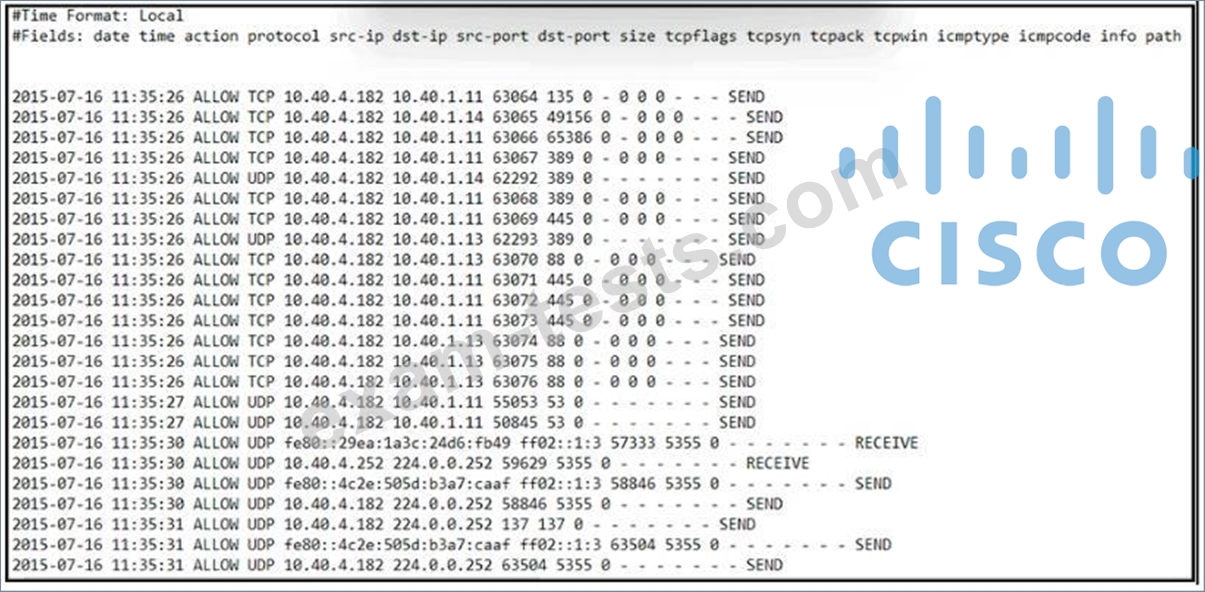
An engineer received an event log file to review. Which technology generated the log?

An engineer received an event log file to review. Which technology generated the log?
Question 140
Which IETF standard technology is useful to detect and analyze a potential security incident by recording session flows that occurs between hosts?