Question 131
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
Question 132
Which category relates to improper use or disclosure of PII data?
Question 133
Which type of evidence supports a theory or an assumption that results from initial evidence?
Question 134
Refer to the exhibit.
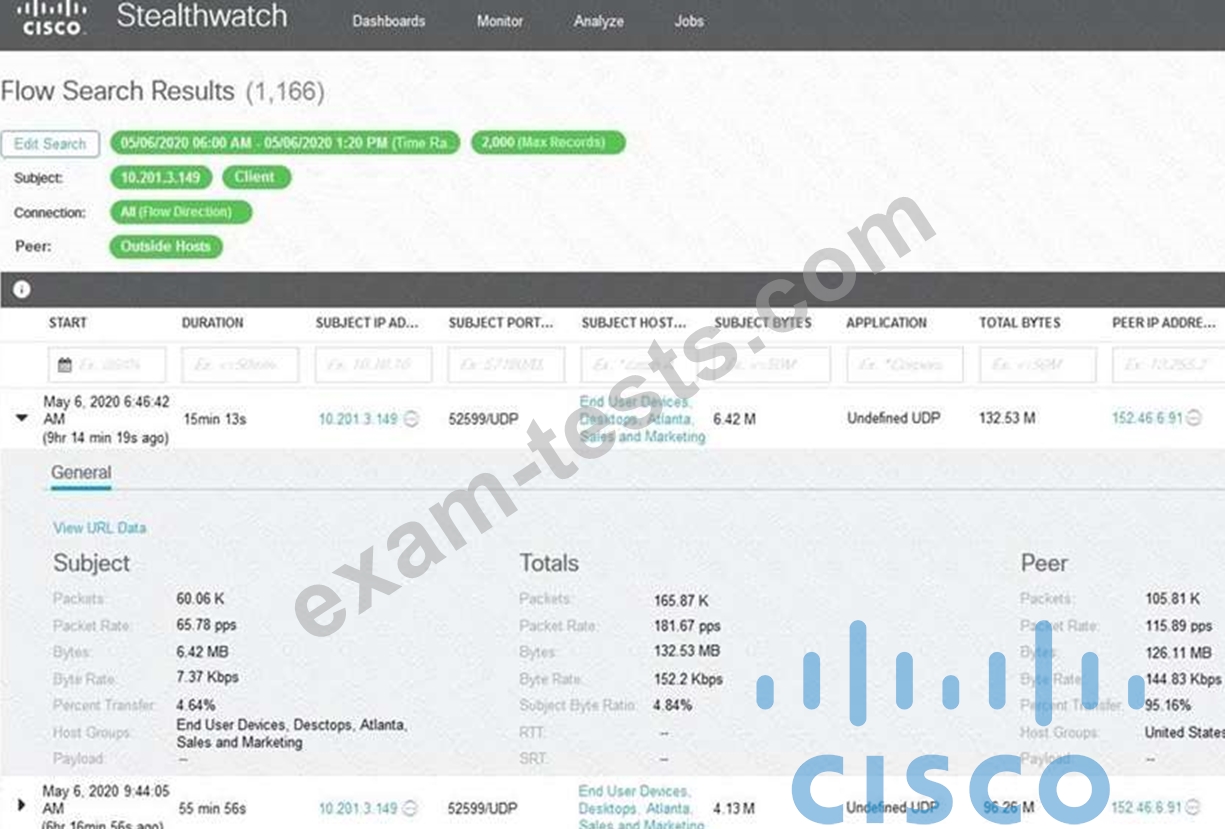
What is the potential threat identified in this Stealthwatch dashboard?

What is the potential threat identified in this Stealthwatch dashboard?
Question 135
At which layer is deep packet inspection investigated on a firewall?

