Question 141
What describes the defense-m-depth principle?
Question 142
Which type of data collection requires the largest amount of storage space?
Question 143
Refer to the exhibit.
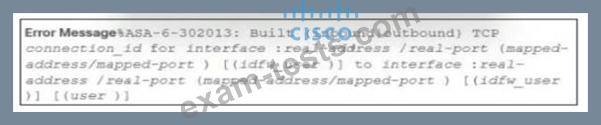
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?

During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
Question 144
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
Question 145
Refer to the exhibit.
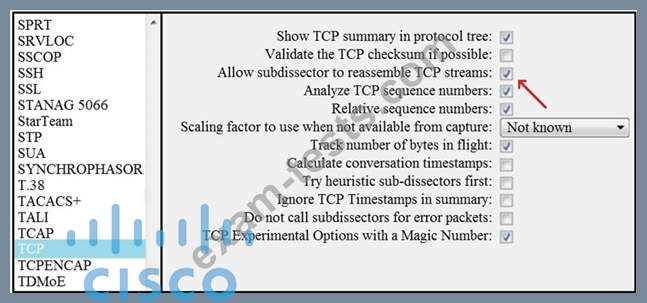
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?

What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?

