Question 66
A software patch has been released to remove vulnerabilities from company's software. A security analyst has been tasked with testing the software to ensure the vulnerabilities have been remediated and the application is still functioning properly. Which of the following tests should be performed NEXT?
Question 67
Which of the following is a best practice with regard to interacting with the media during an incident?
Question 68
When reviewing network traffic, a security analyst detects suspicious activity:
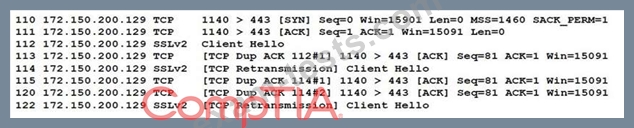
Based on the log above, which of the following vulnerability attacks is occurring?

Based on the log above, which of the following vulnerability attacks is occurring?
Question 69
The security operations team is conducting a mock forensics investigation. Which of the following should be the FIRST action taken after seizing a compromised workstation?
Question 70
An executive tasked a security analyst to aggregate past logs, traffic, and alerts on a particular attack
vector. The analyst was then tasked with analyzing the data and making predictions on future
complications regarding this attack vector. Which of the following types of analysis is the security analyst
MOST likely conducting?
vector. The analyst was then tasked with analyzing the data and making predictions on future
complications regarding this attack vector. Which of the following types of analysis is the security analyst
MOST likely conducting?

