Question 41
Creating a lessons learned report following an incident will help an analyst to communicate which of the following information? (Select TWO)
Question 42
A compliance officer of a large organization has reviewed the firm's vendor management program but has discovered there are no controls defined to evaluate third-party risk or hardware source authenticity. The compliance officer wants to gain some level of assurance on a recurring basis regarding the implementation of controls by third parties.
Which of the following would BEST satisfy the objectives defined by the compliance officer?
(Choose two.)
Which of the following would BEST satisfy the objectives defined by the compliance officer?
(Choose two.)
Question 43
As a proactive threat-hunting technique, hunters must develop situational cases based on likely attack scenarios derived from the available threat intelligence information. After forming the basis of the scenario, which of the following may the threat hunter construct to establish a framework for threat assessment?
Question 44
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL:
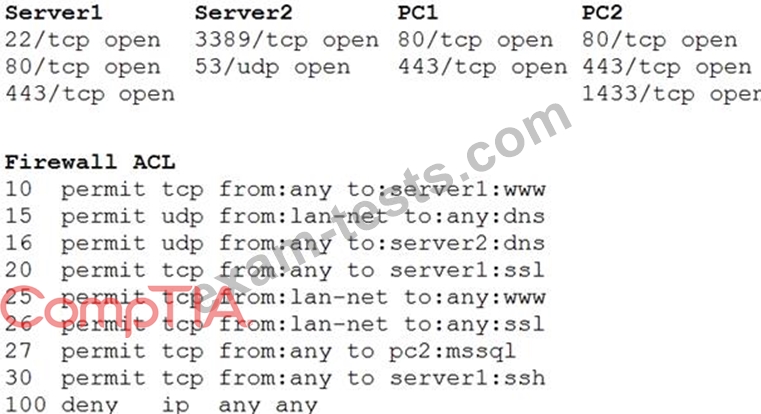
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?

Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?
Question 45
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user.
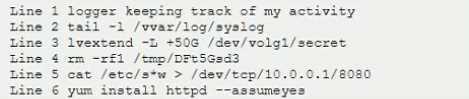
Which of the following commands should the analyst investigate FIRST?

Which of the following commands should the analyst investigate FIRST?

