Question 36
A Chief Information Security Officer (CISO) wants to upgrade an organization's security posture by improving proactive activities associated with attacks from internal and external threats.
Which of the following is the MOST proactive tool or technique that feeds incident response capabilities?
Which of the following is the MOST proactive tool or technique that feeds incident response capabilities?
Question 37
A security analyst needs to identify possible threats to a complex system a client is developing. Which of the following methodologies would BEST address this task?
Question 38
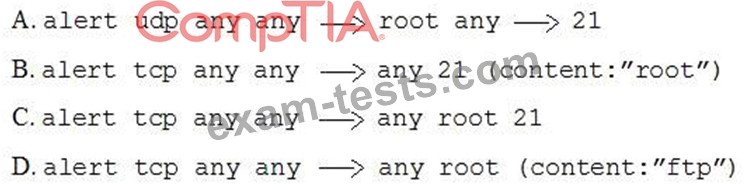
A security administrator needs to create an IDS rule to alert on FTP login attempts by root. Which of the following rules is the BEST solution?

Question 39
A security analyst is reviewing the following log from an email security service.
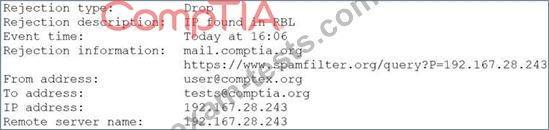
Which of the following BEST describes the reason why the email was blocked?

Which of the following BEST describes the reason why the email was blocked?
Question 40
A security analyst scanned an internal company subnet and discovered a host with the following Nmap output.
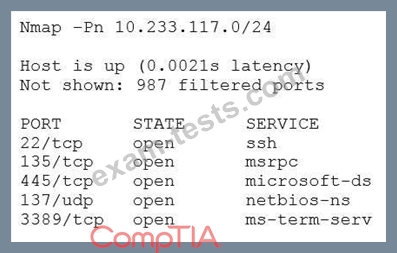
Based on the output of this Nmap scan, which of the following should the analyst investigate FIRST?

Based on the output of this Nmap scan, which of the following should the analyst investigate FIRST?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

