Question 31
The help desk provided a security analyst with a screenshot of a user's desktop:
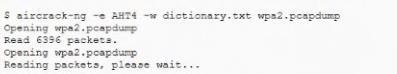
For which of the following is aircrack-ng being used?

For which of the following is aircrack-ng being used?
Question 32
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL:
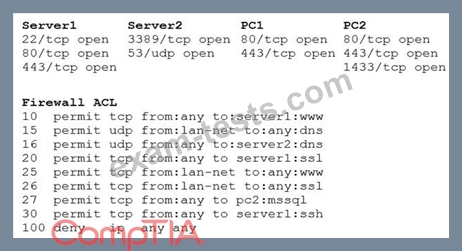
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?

Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?
Question 33
Weeks before a proposed merger is scheduled for completion, a security analyst has noticed unusual traffic patterns on a file server that contains financial information. Routine scans are not detecting the signature of any known exploits or malware. The following entry is seen in the ftp server logs:
tftp *I 10.1.1.1 GET fourthquarterreport.xls
Which of the following is the BEST course of action?
tftp *I 10.1.1.1 GET fourthquarterreport.xls
Which of the following is the BEST course of action?
Question 34
Which of the following types of policies is used to regulate data storage on the network?
Question 35
Company A suspects an employee has been exfiltrating PII via a USB thumb drive. An analyst is tasked with attempting to locate the information on the drive. The PII in question includes the following:

Which of the following would BEST accomplish the task assigned to the analyst?

Which of the following would BEST accomplish the task assigned to the analyst?

