Question 16
An analyst performs a routine scan of a host using Nmap and receives the following output:
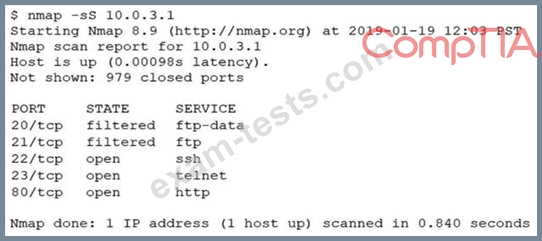
Which of the following should the analyst investigate FIRST?

Which of the following should the analyst investigate FIRST?
Question 17
Given the Nmap request below:
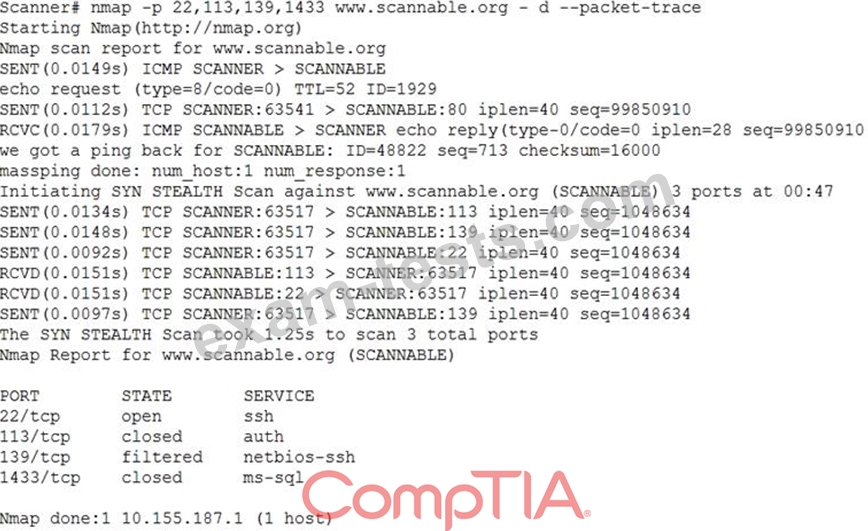
Which of the following actions will an attacker be able to initiate directly against this host?

Which of the following actions will an attacker be able to initiate directly against this host?
Question 18
A security analyst on the threat-hunting team has developed a list of unneeded, benign services that are currently running as part of the standard OS deployment for workstations. The analyst will provide this list to the operations team to create a policy that will automatically disable the services for all workstations in the organization.
Which of the following BEST describes the security analyst's goal?
Which of the following BEST describes the security analyst's goal?
Question 19
An incident responder successfully acquired application binaries off a mobile device for later forensic analysis.
Which of the following should the analyst do NEXT?
Which of the following should the analyst do NEXT?
Question 20
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output:
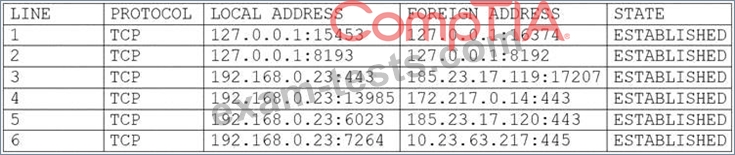
Which of the following lines indicates the computer may be compromised?

Which of the following lines indicates the computer may be compromised?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

