Question 26
A security analyst, who is working for a company that utilizes Linux servers, receives the following results from a vulnerability scan:
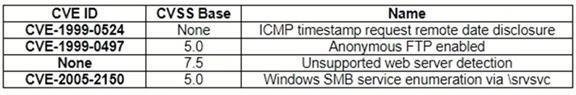
Which of the following is MOST likely a false positive?

Which of the following is MOST likely a false positive?
Question 27
A hacker issued a command and received the following response:
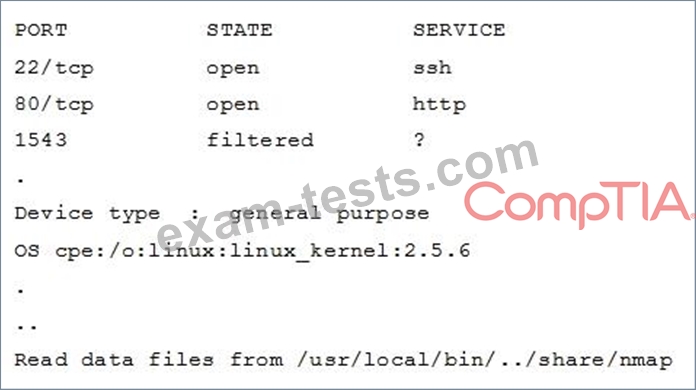
Which of the following describes what the hacker is attempting?

Which of the following describes what the hacker is attempting?
Question 28
The help desk informed a security analyst of a trend that is beginning to develop regarding a suspicious email that has been reported by multiple users. The analyst has determined the email includes an attachment named invoice.zip that contains the following files:
Locky.js
xerty.ini
xerty.lib
Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices. Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices?
Locky.js
xerty.ini
xerty.lib
Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices. Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices?
Question 29
A security analyst was asked to join an outage call for a critical web application. The web middleware support team determined the web server is running and having no trouble processing requests; however, some investigation has revealed firewall denies to the web server that began around 1.00 a.m. that morning. An emergency change was made to enable the access, but management has asked for a root cause determination. Which of the following would be the BEST next step?
Question 30
A security analyst was alerted to a tile integrity monitoring event based on a change to the vhost- paymonts.conf file.
The output of the diff command against the known-good backup reads as follows
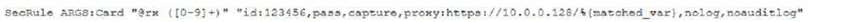
Which of the following MOST likely occurred?
The output of the diff command against the known-good backup reads as follows
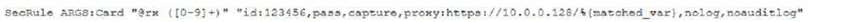
Which of the following MOST likely occurred?

