Question 101
A client has voiced concern about the number of companies being breached by remote attackers, who are looking for trade secrets. Which of the following BEST describes the type of adversaries this would identify?
Question 102
A security consultant is trying to attack a device with a previously identified user account.
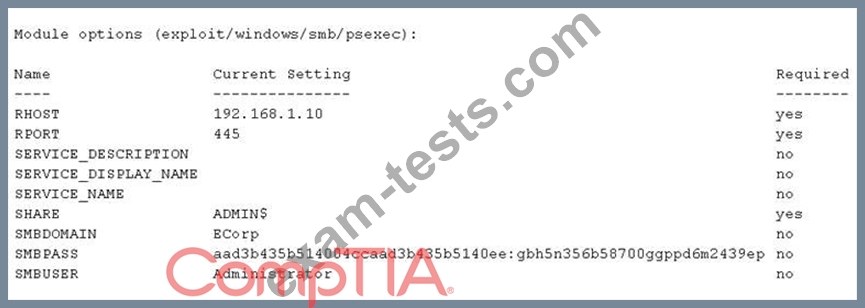
Which of the following types of attacks is being executed?

Which of the following types of attacks is being executed?
Question 103
A penetration tester wants to check manually if a "ghost" vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
Question 104
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses. Which of the following are needed to conduct this scan? (Choose two.)
Question 105
Defining exactly what is to be tested and the results to be generated from the test will help prevent?

