Question 91
During the exploitation phase of a penetration test, a vulnerability is discovered that allows command execution on a Linux web server. A cursory review confirms the system access is only in a low-privilege user context:
www-data. After reviewing, the following output from /etc/sudoers:
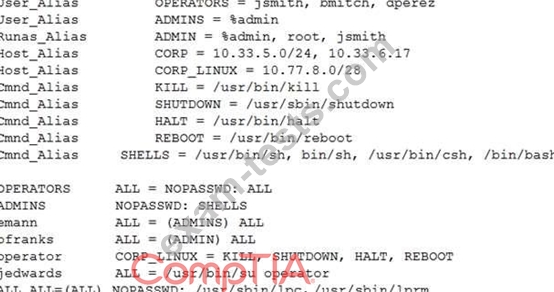
Which of the following users should be targeted for privilege escalation?
www-data. After reviewing, the following output from /etc/sudoers:

Which of the following users should be targeted for privilege escalation?
Question 92
A tester was able to retrieve domain users' hashes. Which of the following tools can be used to uncover the users' passwords? (Choose two.)
Question 93
A company contracted a firm specializing in penetration testing to assess the security of a core business application. The company provided the firm with a copy of the Java bytecode. Which of the following steps must the firm take before it can run a static code analyzer?
Question 94
Given the following script:

Which of the following BEST describes the purpose of this script?

Which of the following BEST describes the purpose of this script?
Question 95
A penetration tester was able to enter an SQL injection command into a text box and gain access to the information store on the database. Which of the following is the BEST recommendation that would mitigate the vulnerability?

