Question 121
During testing, a critical vulnerability is discovered on a client's core server. Which of the following should be the NEXT action?
Question 122
A recently concluded penetration test revealed that a legacy web application is vulnerable lo SQL injection Research indicates that completely remediating the vulnerability would require an architectural change, and the stakeholders are not m a position to risk the availability of the application Under such circumstances, which of the following controls are low-effort, short-term solutions to minimize the SQL injection risk? (Select TWO).
Question 123
During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell back to the attacking machine at 192.168.1.5. Which of the following are possible ways to do so? (Select TWO).
Question 124
A penetration tester reviews the scan results of a web application. Which of the following vulnerabilities is MOST critical and should be prioritized for exploitation?
Question 125
D18912E1457D5D1DDCBD40AB3BF70D5D
During the exploitation phase of a penetration test, a vulnerability is discovered that allows command execution on a Linux web server. A cursory review confirms the system access is only in a low-privilege user context: www-dat a. After reviewing, the following output from /etc/sudoers:
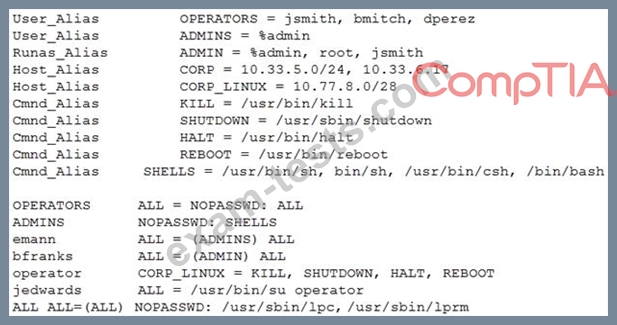
Which of the following users should be targeted for privilege escalation?
During the exploitation phase of a penetration test, a vulnerability is discovered that allows command execution on a Linux web server. A cursory review confirms the system access is only in a low-privilege user context: www-dat a. After reviewing, the following output from /etc/sudoers:

Which of the following users should be targeted for privilege escalation?

