Question 116
A penetration tester is reviewing the following output from a wireless sniffer:
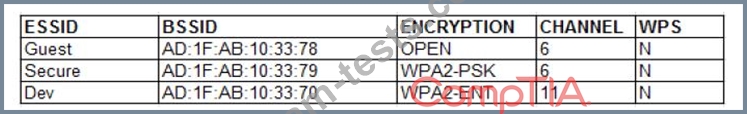
Which of the following can be extrapolated from the above information?

Which of the following can be extrapolated from the above information?
Question 117
D18912E1457D5D1DDCBD40AB3BF70D5D
Which of the following is the MOST comprehensive type of penetration test on a network?
Which of the following is the MOST comprehensive type of penetration test on a network?
Question 118
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikazt. Which of the following registry changes would allow for credential caching in memory?
A)
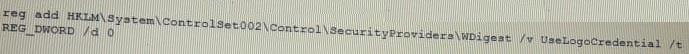
B)
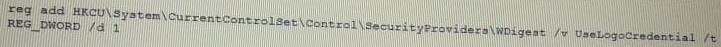
C)
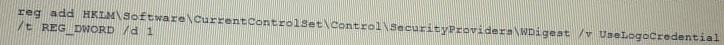
D)
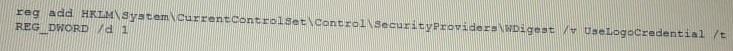
A)

B)

C)

D)

Question 119
During an internal network penetration test the tester is able to compromise a Windows system and recover the NTLM hash for a local wrltsrnAdrain account Attempting to recover the plaintext password by cracking the hash has proved to be unsuccessful, and the tester has decided to try a pass-the-hash attack to see if the credentials are reused on other in-scope systems Using the Medusa tool the tester attempts to authenticate to a list of systems, including the originally compromised host, with no success Given the output below:
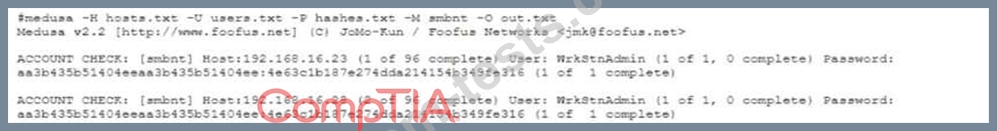
Which of the following Medusa commands would potentially provide better results?

Which of the following Medusa commands would potentially provide better results?
Question 120
An attacker uses SET to make a copy of a company's cloud-hosted web mail portal and sends an email m to obtain the CEO s login credentials Which of the following types of attacks is this an example of?

