Question 136
A penetration tester has performed a pivot to a new Linux device on a different network. The tester writes the following command:
for m in {1..254..1};do ping -c 1 192.168.101.$m; done
Which of the following BEST describes the result of running this command?
for m in {1..254..1};do ping -c 1 192.168.101.$m; done
Which of the following BEST describes the result of running this command?
Question 137
If a security consultant comes across a password hash that resembles the following b117 525b3454 7Oc29ca3dBaeOb556ba8 Which of the following formats is the correct hash type?
Question 138
After an Nmap NSE scan, a security consultant is seeing inconsistent results while scanning a host. Which of the following is the MOST likely cause?
Question 139
A penetration tester ran an Nmap scan against a target and received the following output:
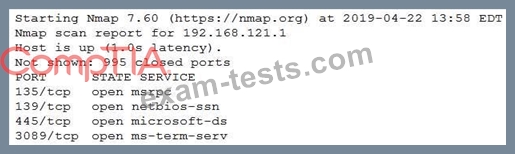
Which of the following commands would be best for the penetration tester to execute NEXT to discover any weaknesses or vulnerabilities?

Which of the following commands would be best for the penetration tester to execute NEXT to discover any weaknesses or vulnerabilities?
Question 140
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses. Which of the following are needed to conduct this scan? (Choose two.).

