Question 131
A penetration tester executes the following commands:
C:\>%userprofile%\jtr.exe
This program has been blocked by group policy
C:\> accesschk.exe -w -s -q -u Users C:\Windows
rw C:\Windows\Tracing
C:\>copy %userprofile%\jtr.exe C:\Windows\Tracing
C:\Windows\Tracing\jtr.exe
jtr version 3.2...
jtr>
Which of the following is a local host vulnerability that the attacker is exploiting?
C:\>%userprofile%\jtr.exe
This program has been blocked by group policy
C:\> accesschk.exe -w -s -q -u Users C:\Windows
rw C:\Windows\Tracing
C:\>copy %userprofile%\jtr.exe C:\Windows\Tracing
C:\Windows\Tracing\jtr.exe
jtr version 3.2...
jtr>
Which of the following is a local host vulnerability that the attacker is exploiting?
Question 132
A penetration tester notices that the X-Frame-Optjons header on a web application is not set. Which of the following would a malicious actor do to exploit this configuration setting?
Question 133
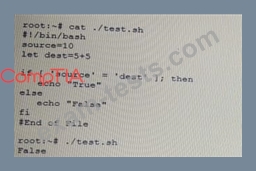
A penetration tester is checking a script to determine why some basic persisting. The expected result was the program outputting "True."
\
Given the output from the console above, which of the following explains how to correct the errors in the script? (Select TWO)

\
Given the output from the console above, which of the following explains how to correct the errors in the script? (Select TWO)
Question 134
While trying to maintain persistence on a Windows system with limited privileges, which of the following registry keys should the tester use?
Question 135
Given the following Python script:
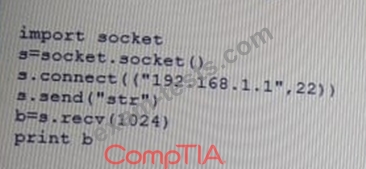
Which of the following actions will it perform?

Which of the following actions will it perform?

