Question 126
Which of the following has a direct and significant impact on the budget of the security assessment?
Question 127
A vulnerability scan report shows what appears to be evidence of a memory disclosure vulnerability on one of the target hosts. The administrator claims the system is patched and the evidence is a false positive.
Which of the following is the BEST method for a tester to confirm the vulnerability exists?
Which of the following is the BEST method for a tester to confirm the vulnerability exists?
Question 128
A penetration tester is required to perform OSINT on staff at a target company after completing the infrastructure aspect. Which of the following would be the BEST step for the penetration tester to take?
Question 129
While reviewing logs, a web developer notices the following user input string in a field:
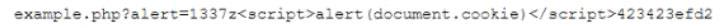
Which of the following types of attacks was done to the website?
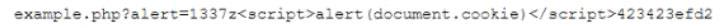
Which of the following types of attacks was done to the website?
Question 130
A penetration tester executes the following commands:
C:\>%userprofile%\jtr.exe
This program has been blocked by group policy
C:\> accesschk.exe -w -s -q -u Users C:\Windows
rw C:\Windows\Tracing
C:\>copy %userprofile%\jtr.exe C:\Windows\Tracing
C:\Windows\Tracing\jtr.exe
jtr version 3.2...
jtr>
Which of the following is a local host vulnerability that the attacker is exploiting?
C:\>%userprofile%\jtr.exe
This program has been blocked by group policy
C:\> accesschk.exe -w -s -q -u Users C:\Windows
rw C:\Windows\Tracing
C:\>copy %userprofile%\jtr.exe C:\Windows\Tracing
C:\Windows\Tracing\jtr.exe
jtr version 3.2...
jtr>
Which of the following is a local host vulnerability that the attacker is exploiting?

