Question 61
A system administrator recently deployed and verified the installation of a critical patch issued by the company's primary OS vendor. This patch was supposed to remedy a vulnerability that would allow an adversary to remotely execute code from over the network. However, the administrator just ran a vulnerability assessment of networked systems, and each of them still reported having the same vulnerability. Which of the following if the MOST likely explanation for this?
Question 62
Using a heuristic system to detect an anomaly in a computer's baseline, a system administrator was able
to detect an attack even though the company signature based IDS and antivirus did not detect it. Further
analysis revealed that the attacker had downloaded an executable file onto the company PC from the USB
port, and executed it to trigger a privilege escalation flaw. Which of the following attacks has MOST likely
occurred?
to detect an attack even though the company signature based IDS and antivirus did not detect it. Further
analysis revealed that the attacker had downloaded an executable file onto the company PC from the USB
port, and executed it to trigger a privilege escalation flaw. Which of the following attacks has MOST likely
occurred?
Question 63
When reviewing network traffic, a security analyst detects suspicious activity:
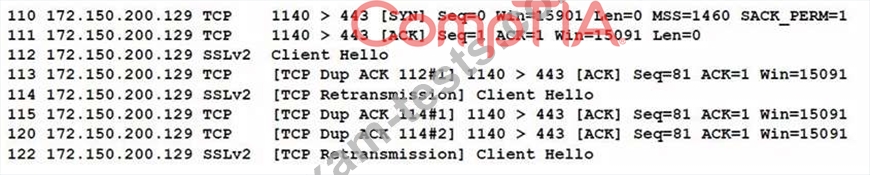
Based on the log above, which of the following vulnerability attacks is occurring?

Based on the log above, which of the following vulnerability attacks is occurring?
Question 64
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team. Which of the following frameworks would BEST support the program? (Select two.)
Question 65
An organization uses Common Vulnerability Scoring System (CVSS) scores to prioritize remediation of
vulnerabilities.
Management wants to modify the priorities based on a difficulty factor so that vulnerabilities with lower
CVSS scores may get a higher priority if they are easier to implement with less risk to system functionality.
Management also wants to quantify the priority. Which of the following would achieve management's
objective?
vulnerabilities.
Management wants to modify the priorities based on a difficulty factor so that vulnerabilities with lower
CVSS scores may get a higher priority if they are easier to implement with less risk to system functionality.
Management also wants to quantify the priority. Which of the following would achieve management's
objective?

