Question 6
A security analyst is reviewing a report from the networking department that describes an increase in network utilization, which is causing network performance issues on some systems. A top talkers report over a five-minute sample is included.
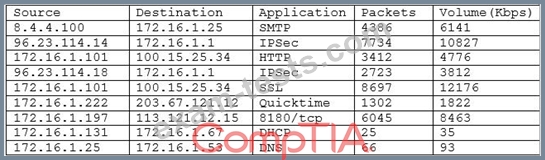
Given the above output of the sample, which of the following should the security analyst accomplish FIRST to help track down the performance issues?

Given the above output of the sample, which of the following should the security analyst accomplish FIRST to help track down the performance issues?
Question 7
A security professional is analyzing the results of a network utilization report. The report includes the following information:
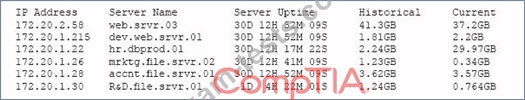
Which of the following servers needs further investigation?

Which of the following servers needs further investigation?
Question 8
During a routine review of firewall logs, an analyst identified that an IP address from the organization's server subnet had been connecting during nighttime hours to a foreign IP address, and had been sending between 150 and 500 megabytes of data each time. This had been going on for approximately one week, and the affected server was taken offline for forensic review. Which of the following is MOST likely to drive up the incident's impact assessment?
Question 9
A cybersecurity analyst has identified a new mission-essential function that utilizes a public cloud-based system. The analyst needs to classify the information processed by the system with respect to CIA. Which of the following should provide the CIA classification for the information?
Question 10
A newly discovered malware has a known behavior of connecting outbound to an external destination on
port 27500 for the purposes of exfiltrating data. The following are four snippets taken from running
netstat -anon separate Windows workstations:
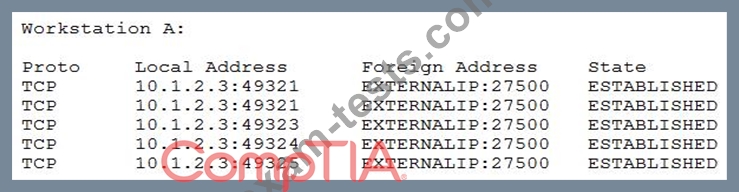



Based on the above information, which of the following is MOST likely to be exposed to this malware?
port 27500 for the purposes of exfiltrating data. The following are four snippets taken from running
netstat -anon separate Windows workstations:




Based on the above information, which of the following is MOST likely to be exposed to this malware?

