Question 11
After running a packet analyzer on the network, a security analyst has noticed the following output:
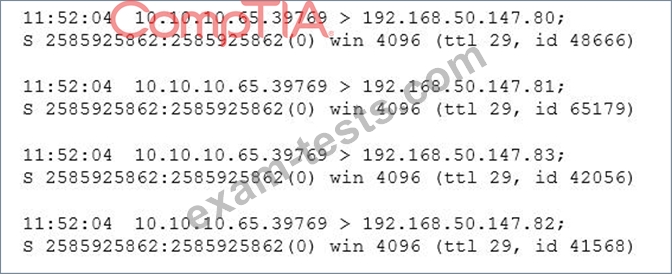
Which of the following is occurring?

Which of the following is occurring?
Question 12
A vulnerability scan has returned the following information:
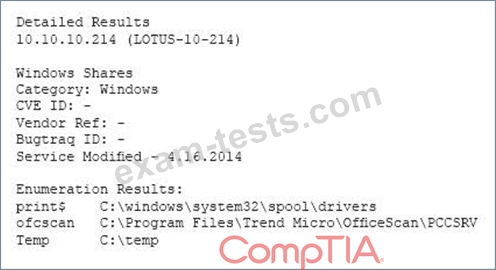
Which of the following describes the meaning of these results?

Which of the following describes the meaning of these results?
Question 13
A company has recently launched a new billing invoice website for a few key vendors. The cybersecurity analyst is receiving calls that the website is performing slowly and the pages sometimes time out. The analyst notices the website is receiving millions of requests, causing the service to become unavailable.
Which of the following can be implemented to maintain the availability of the website?
Which of the following can be implemented to maintain the availability of the website?
Question 14
A technician is troubleshooting a desktop computer with low disk space. The technician reviews the following information snippets:

Which of the following should the technician do to BEST resolve the issue based on the above information?
(Choose two.)

Which of the following should the technician do to BEST resolve the issue based on the above information?
(Choose two.)
Question 15
A security analyst is reviewing logs and discovers that a company-owned computer issued to an employee is generating many alerts and warnings. The analyst continues to review the log events and discovers that a non-company-owned device from a different, unknown IP address is generating the same events. The analyst informs the manager of these findings, and the manager explains that these activities are already known and part of an ongoing events. Given this scenario, which of the following roles are the analyst, the employee, and the manager filling?

