Question 41
A company installed a wireless network more than a year ago, standardizing on the same model APs in a single subnet. Recently, several users have reported timeouts and connection issues with Internet browsing. The security administrator has gathered some information about the network to try to recreate the issues with the assistance of a user. The administrator is able to ping every device on the network and confirms that the network is very slow.
Output:
Given the above results, which of the following should the administrator investigate FIRST?

Output:

Given the above results, which of the following should the administrator investigate FIRST?
Question 42
A penetration test for the Internal DNS service of a company is scheduled, and the security analyst uses the ccpdump udp port S3 -1 ech0 command to get a packet capture from the DNS server that will be used to confirm any findings During the daily report meeting the penetration tester reports a zone transfer vulnerability using the dig -axfr command against the server The analyst opens the packet capture from the day before, but there are no traces of the transfer. Which of the following is the MOST likely cause of this issue?
Question 43
A recent audit has uncovered several coding errors and a lack of input validation being used on a public portal.
Due to the nature of the portal and the severity of the errors, the portal is unable to be patched. Which of the following tools could be used to reduce the risk of being compromised?
Due to the nature of the portal and the severity of the errors, the portal is unable to be patched. Which of the following tools could be used to reduce the risk of being compromised?
Question 44
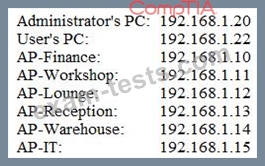
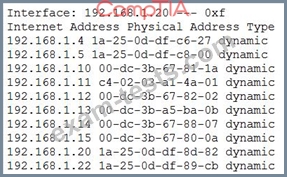
During a review of security controls, an analyst was able to connect to an external, unsecured FTP server from a workstation. The analyst was troubleshooting and reviewed the ACLs of the segment firewall the workstation is connected to:

Based on the ACLs above, which of the following explains why the analyst was able to connect to the FTP server?

Based on the ACLs above, which of the following explains why the analyst was able to connect to the FTP server?
Question 45
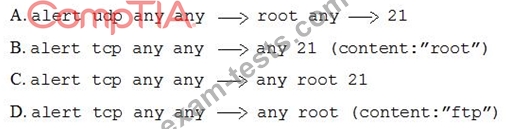
A security administrator needs to create an IDS rule to alert on FTP login attempts by root. Which of the following rules is the BEST solution?