Question 21
Datacenter access is controlled with proximity badges that record all entries and exits from the datacenter.
The access records are used to identify which staff members accessed the data center in the event of equipment theft.
Which of the following MUST be prevented in order for this policy to be effective?
The access records are used to identify which staff members accessed the data center in the event of equipment theft.
Which of the following MUST be prevented in order for this policy to be effective?
Question 22
A security analyst has noticed an alert from the SIEM. A workstation is repeatedly trying to connect to port
445 of a file server on the production network. All of the attempts are made with invalid credentials. Which
of the following describes what is occurring?
445 of a file server on the production network. All of the attempts are made with invalid credentials. Which
of the following describes what is occurring?
Question 23
After completing a vulnerability scan, the following output was noted:
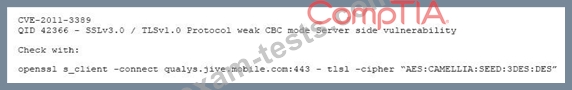
Which of the following vulnerabilities has been identified?

Which of the following vulnerabilities has been identified?
Question 24
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:
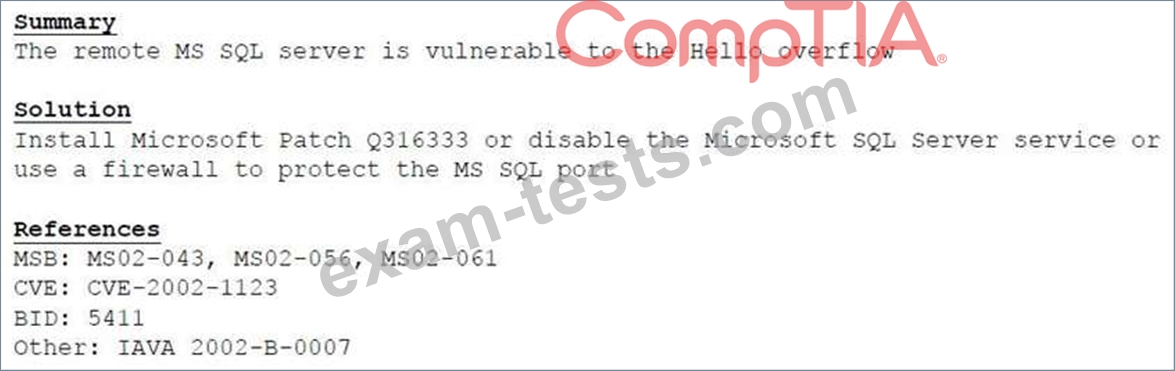
Based on the above information, which of the following should the system administrator do? (Select TWO).

Based on the above information, which of the following should the system administrator do? (Select TWO).
Question 25
A security analyst is monitoring authentication exchanges over the company's wireless network. A sample of the Wireshark output is shown below:
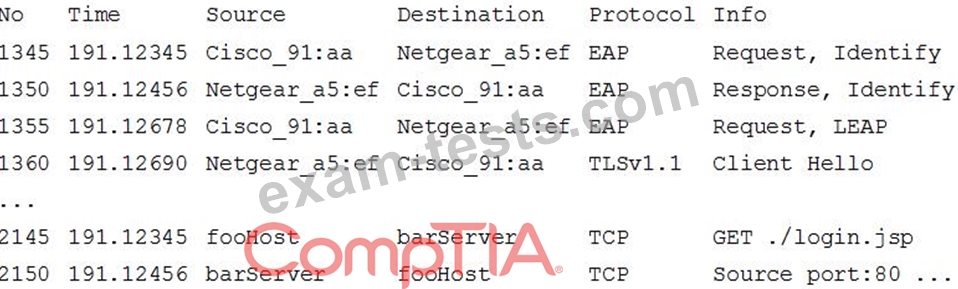
Which of the following would improve the security posture of the wireless network?

Which of the following would improve the security posture of the wireless network?

