Question 16
Alerts have been received from the SIEM, indicating infections on multiple computers. Based on threat characteristic, these files were quarantined by the host-based antivirus program. At the same time, additional alerts in the SIEM show multiple blocked URLs from the address of the infected computers; the URLs were clashed as uncategorized. The domain location of the IP address of the URLs that were blocked is checked, and it is registered to an ISP in Russia. Which of the following steps should be taken NEXT?
Question 17
During an investigation, a computer is being seized. Which of the following is the FIRST step the analyst
should take?
should take?
Question 18
A security analyst has determined that the user interface on an embedded device is vulnerable to common SQL injections. The device is unable to be replaced, and the software cannot be upgraded.
Which of the following should the security analyst recommend to add additional security to this device?
Which of the following should the security analyst recommend to add additional security to this device?
Question 19
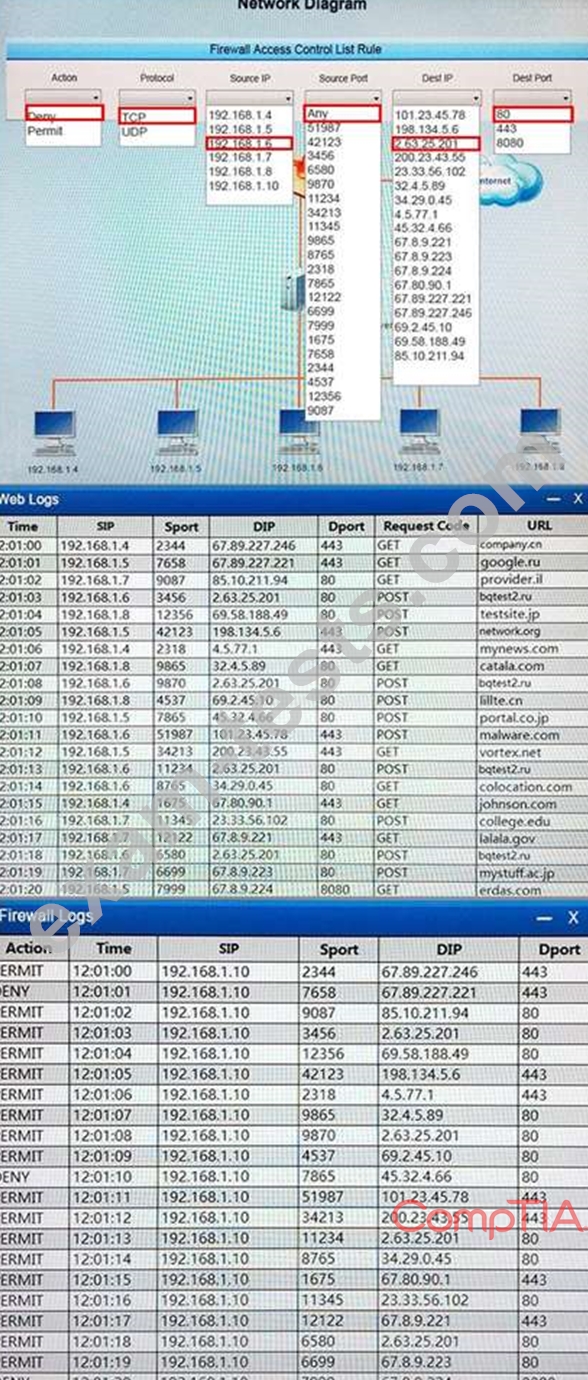
A security analyst suspects that a workstation may be beaconing to a command and control server. Inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
Modify the firewall ACL, using the Firewall ACL form to mitigate the issue.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button.
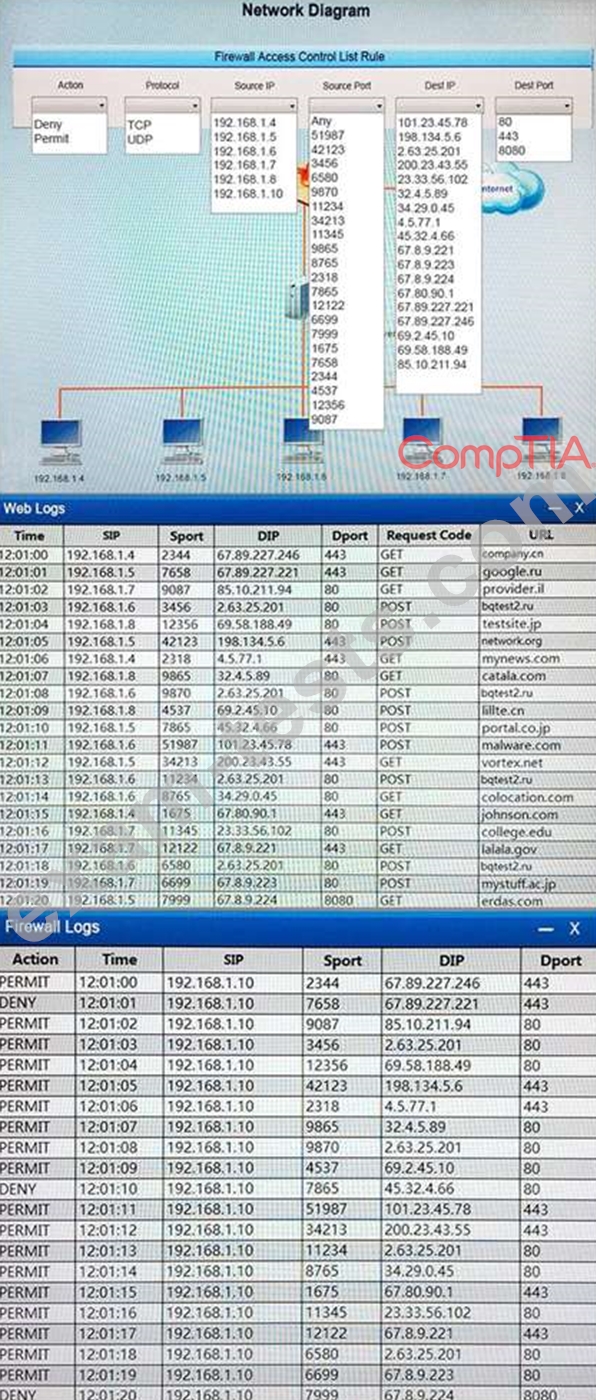
Instructions:
Modify the firewall ACL, using the Firewall ACL form to mitigate the issue.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button.

Question 20
Which of the following actions should occur to address any open issues while closing an incident involving various departments within the network?