Question 6
A security engineer is reviewing security products that identify malicious actions by users as part of a company's insider threat program. Which of the following is the MOST appropriate product category for this purpose?
Question 7
A system administrator has reviewed the following output:
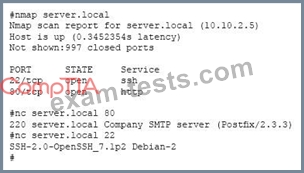
Which of the following can a system administrator infer from the above output?

Which of the following can a system administrator infer from the above output?
Question 8
Which of the following is the MOST important objective of a post-incident review?
Question 9
The Dirty COW attack is an example of what type of vulnerability?
Question 10
A threat feed notes malicious actors have been infiltrating companies and exfiltration data to a specific set of domains Management at an organization wants to know if it is a victim Which of the following should the security analyst recommend to identity this behavior without alerting any potential malicious actors?

