Question 106
Which of the following documents BEST describes the manner in which a security assessment will be conducted?
Question 107
A penetration tester reports an application is only utilizing basic authentication on an Internet-facing application.
Which of the following would be the BEST remediation strategy?
Which of the following would be the BEST remediation strategy?
Question 108
During an engagement an unsecure direct object reference vulnerability was discovered that allows the extraction of highly sensitive PII. The tester is required to extract and then exfil the information from a web application with identifiers 1 through 1000 inclusive. When running the following script, an error is encountered:
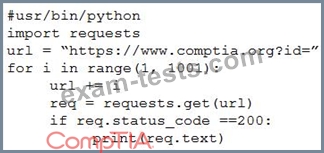
Which of the following lines of code is causing the problem?

Which of the following lines of code is causing the problem?
Question 109
A penetration tester has identified a directory traversal vulnerability. Which of the following payloads could have helped the penetration tester identify this vulnerability?
Question 110
A penetration tester is testing a banking application and uncovers a vulnerability. The tester is logged in as a non-privileged user who should have no access to any data. Given the data below from the web interception proxy Request POST /Bank/Tax/RTSdocuments/ HTTP 1.1 Host: test.com Accept: text/html; application/xhtml+xml Referrer: https://www.test.com/Bank/Tax/RTSdocuments/ Cookie: PHPSESSIONID: ; Content-Type: application/form-data; Response
403 Forbidden
<tr>
<td> Error:</td></tr>
<tr><td> Insufficient Privileges to view the data. </td></tr>
Displaying 1-10 of 105 records
Which of the following types of vulnerabilities is being exploited?
403 Forbidden
<tr>
<td> Error:</td></tr>
<tr><td> Insufficient Privileges to view the data. </td></tr>
Displaying 1-10 of 105 records
Which of the following types of vulnerabilities is being exploited?

