Question 111
Which of the following commands will allow a tester to enumerate potential unquoted services paths on a host?
Question 112
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
Question 113
Which of the following reasons does penetration tester needs to have a customer's point-of -contact information available at all time? (Select THREE).
Question 114
A penetration tester wants to check manually if a "ghost" vulnerability exists in a system.
Which of the following methods is the correct way to validate the vulnerability?
A)
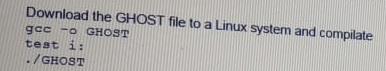
B)
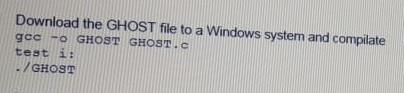
C)
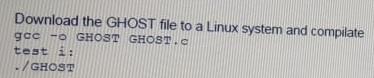
D)
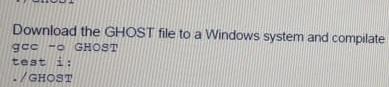
Which of the following methods is the correct way to validate the vulnerability?
A)

B)

C)

D)

Question 115
After successfully capturing administrator credentials to a remote Windows machine, a penetration tester attempts to access the system using PSExec but is denied permission. Which of the following shares must be accessible for a successful PSExec connection?

