Question 46
An HR employee began having issues with a device becoming unresponsive after attempting to open an email attachment. When informed, the security analyst became suspicious of the situation, even though there was not any unusual behavior on the IDS or any alerts from the antivirus software. Which of the following BEST describes the type of threat in this situation?
Question 47
A vulnerability scan returned the following results for a web server that hosts multiple wiki sites:
Apache-HTTPD-cve-2014-023: Apache HTTPD: mod_cgid denial of service CVE-2014-
0231
Due to a flaw found in mog_cgid, a server using mod_cgid to host CGI scripts could be vulnerable to a
DoS attack caused by a remote attacker who is exploiting a weakness in non-standard input, causing
processes to hang indefinitely.
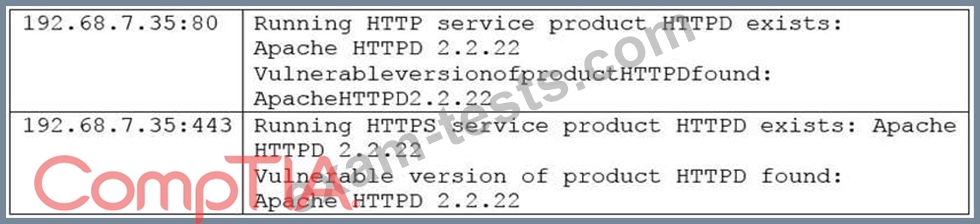
The security analyst has confirmed the server hosts standard CGI scripts for the wiki sites, does not have
mod_cgid installed, is running Apache 2.2.22, and is not behind a WAF. The server is located in the DMZ,
and the purpose of the server is to allow customers to add entries into a publicly accessible database.
Which of the following would be the MOST efficient way to address this finding?
Apache-HTTPD-cve-2014-023: Apache HTTPD: mod_cgid denial of service CVE-2014-
0231
Due to a flaw found in mog_cgid, a server using mod_cgid to host CGI scripts could be vulnerable to a
DoS attack caused by a remote attacker who is exploiting a weakness in non-standard input, causing
processes to hang indefinitely.

The security analyst has confirmed the server hosts standard CGI scripts for the wiki sites, does not have
mod_cgid installed, is running Apache 2.2.22, and is not behind a WAF. The server is located in the DMZ,
and the purpose of the server is to allow customers to add entries into a publicly accessible database.
Which of the following would be the MOST efficient way to address this finding?
Question 48
An organization has two environments: development and production. Development is where applications are developed with unit testing. The development environment has many configuration differences from the production environment. All applications are hosted on virtual machines. Vulnerability scans are performed against all systems before and after any application or configuration changes to any environment. Lately, vulnerability remediation activity has caused production applications to crash and behave unpredictably. Which of the following changes should be made to the current vulnerability management process?
Question 49
A system administrator has reviewed the following output:
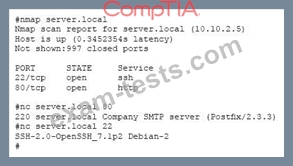
Which of the following can a system administrator infer from the above output?

Which of the following can a system administrator infer from the above output?
Question 50
A security analyst is making recommendations for securing access to the new forensic workstation and workspace. Which of the following security measures should the analyst recommend to protect access to forensic data?
Premium Bundle
Newest CS0-001 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-001 Exam! BraindumpsPass.com now offer the updated CS0-001 exam dumps, the BraindumpsPass.com CS0-001 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-001 pdf dumps with Exam Engine here:

