Question 56
A hacker issued a command and received the following response:

Which of the following describes what the hacker is attempting?

Which of the following describes what the hacker is attempting?
Question 57
An analyst wants to use a command line tool to identify open ports and running services on a host along
with the application that is associated with those services and port. Which of the following should the
analyst use?
with the application that is associated with those services and port. Which of the following should the
analyst use?
Question 58
A recent vulnerability scan found four vulnerabilities on an organization's public Internet-facing IP addresses. Prioritizing in order to reduce the risk of a breach to the organization, which of the following should be remediated FIRST?
Question 59
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:
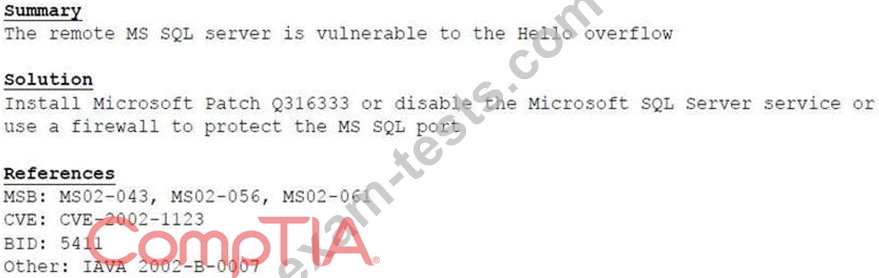
Based on the above information, which of the following should the system administrator do? (Select TWO).

Based on the above information, which of the following should the system administrator do? (Select TWO).
Question 60
A nuclear facility manager (determined the need to monitor utilization of water within the facility. A startup company just announced a state-of-the-art solution to address the need for integrality 'be business and ICS networks The solution leqmies a very small agent lo be installed on the 1CS equipment Which of the following is the MOST important security control for the manager to invest in to protect the facility?

